当前位置:网站首页>Possible security vulnerabilities in NFT
Possible security vulnerabilities in NFT
2022-06-22 20:16:00 【Blockchain Star Club】
Blockchain 、NFT And others have been loved and trusted by people with high security , however , High security does not mean absolute security , There are always many loopholes in the Internet , Network hackers are eyeing it .
in fact , Even in places known for their safety NFT in , We have also encountered many cases of asset theft . Hackers use NFT Loopholes in smart contracts , Attack the user account or platform , Only this year , There have been several large-scale security incidents .
NFT There are two types of security vulnerabilities in , One is its own vulnerability , The other is the business vulnerability from the platform .
Its own loopholes
NFT The whole process includes casting 、 issue 、 The circulation 、 Destruction and other stages . There are basically no problems in the casting and destruction stages ,NFT The security problems of the company mainly focus on the issue and circulation .
NFT The circulation mainly involves the security of the circulation address , In this respect, there may be more “ phishing ” And other potential safety hazards , There are relatively few contractual loopholes .

The release phase is one of the most vulnerable phases . Generally speaking ,NFT The issue will be divided into pre-sale and formal sale . At pre-sale , The project party will provide users with pre-sale qualification through the white list . A common way is for hackers to exploit vulnerabilities in the white list , Bypass restrictions , Get pre sold NFT.
The platform's verification vulnerability to the white list led to NFT The project was attacked , such as APE Coin Airdrop incident 、NBA The two typical cases of the Hoover incident are the security problems caused by the white list vulnerability . The former is due to white list verification , Only verify that the user is right NFT The instantaneous state of ownership , Therefore, hackers use the method of lightning loan , A large number of NFT, After the final repayment of the lightning loan , Will make a profit APE Coin To transfer ; The latter is due to insufficient review when verifying the user's signature , Generally speaking , A signature can only be used once , but NBA Project party's NFT Verified vulnerability , Make the signature reusable , Finally, one signature can receive multiple NFT.

Platform vulnerabilities
NFT The platform is also vulnerable to vulnerabilities , The most typical one is right NFT The protocol standard for . Although they are collectively referred to as NFT, But not all NFT All adopt the same standard . classical ERC-721, It was born later ERC-1155、ERC-998 etc. , All are NFT Common protocol . such as TreasureDAO In a security incident , Just confused ERC-721 and ERC -1155 The difference between , It leads to logic confusion , Finally, it gives hackers an opportunity .
in addition , There are also platforms that will NFT As a kind of liquidity asset token or loan collateral, etc , If these platforms are used during business execution , Inspection is not fully considered - Interaction, etc , It is very easy to lead to loopholes in the business process , Security issues arise .
Summary
NFT The security incidents that occur from time to time in the market remind us , There is no absolute safety “ RIZ-ZOAWD ”. therefore , We are choosing NFT when , We should be more cautious , Do not invest blindly , At the same time, they also need to constantly enrich their relevant knowledge , Make it easier to avoid projects or platforms with potential security risks .
边栏推荐
- 【深入理解TcaplusDB知識庫】部署TcaplusDB Local版常見問題
- [in depth understanding of tcapulusdb technology] new models of tcapulusdb
- 【深入理解TcaplusDB技术】单据受理之创建业务指南
- 51万奖池邀你参战!第二届阿里云ECS CloudBuild开发者大赛来袭
- 【深入理解TcaplusDB技术】TcaplusDB 表管理——清理表
- 防火墙基础之安全策略和NAT(Easy IP)
- 【深入理解TcaplusDB技术】运维平台中实现TcaplusDB事务管理
- 一文带你读懂内存泄露
- R语言数据预处理、把类型变量转化为因子变量,把数据集转化为h2o格式、数据集划分(训练集、测试集、验证集)
- [in depth understanding of tcaplus DB technology] Introduction to tcaplus JDBC development
猜你喜欢

树、森林及二叉树的相互转换

client-go gin的简单整合十一-Delete
![Summer Challenge [FFH] Hongmeng machine learning journey from scratch NLP emotion analysis](/img/e8/3b6de6445c9a78f33c8e91c2ff5517.png)
Summer Challenge [FFH] Hongmeng machine learning journey from scratch NLP emotion analysis

matplotlib设置坐标轴刻度间隔

How should programmers look up dates

图的定义及术语
![[in depth understanding of tcaplus DB technology] getting started tcaplus SQL driver](/img/2b/3ab5e247ac103728b4d3579c3c5468.png)
[in depth understanding of tcaplus DB technology] getting started tcaplus SQL driver

【深入理解TcaplusDB技术】入门MySQL Driver
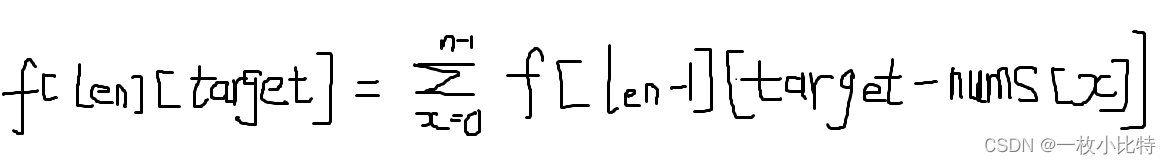
完全背包如何考虑排列问题

年中大促 | 集成无忧,超值套餐 6 折起
随机推荐
【深入理解TcaplusDB技术】运维平台中实现TcaplusDB事务管理
Be careful with MySQL filesort
基于Sentinel的高可用限流系统的Grafana报表展示
佐治亚理工学院|具有服务质量保证的多无人机野火协同覆盖和跟踪规划
第六章 操作位和位串(二)
IDEA写jsp代码报错,但是正常运行解决
[deeply understand tcapulusdb technology] tcapulusdb table management - delete table
不断重修的计划与变化
Classic interview question: a page from entering URL to rendering process
【深入理解TcaplusDB技术】TcaplusDB机型管理
[in depth understanding of tcapulusdb technology] getting started with MySQL driver
Nlp-d57-nlp competition D26 & skimming questions D13 & reading papers & finding bugs for more than an hour
【小资说库】掰扯下概念:数据、数据库、数据库系统、数据库管理系统、数据库技术
数字经济加速落地,能为中小企业带来什么?
关于放大器失真的原因你了解多少呢?
美图稳定性和运维保障方案
C语言实现平衡二叉树
[deeply understand tcapulusdb technology] tcapulusdb table management - rebuild table
【深入理解TcaplusDB知識庫】部署TcaplusDB Local版常見問題
【深入理解TcaplusDB技术】TcaplusDB机器如何下架