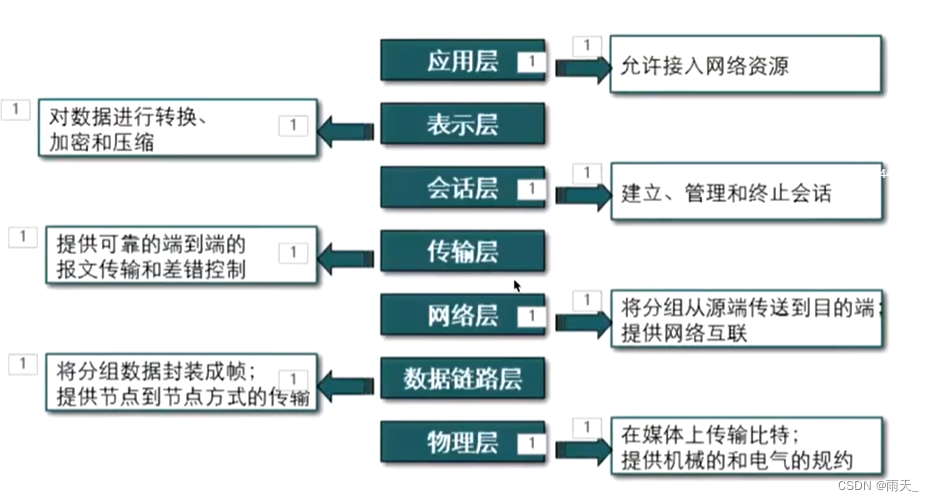
当前位置:网站首页>Nowcodertop7-11 - continuous updating
Nowcodertop7-11 - continuous updating
2022-07-25 11:17:00 【Wang Xixi-】
TOP7 The entry node of a link in a list
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-7sq4R3XY-1658559347669)(D:\desktop\bite\mdpng\image-20220721153418821.png)]](/img/8c/629964619a785c10f762544955d6e5.png)
/** * 7 The entry node of a link in a list * Suppose that there is a total of a individual , The nodes in the ring are b individual , set up fast The number of nodes passed by the pointer is f,slow The number of nodes passed by the pointer is s, Then there are two conclusions : * f = 2 * s ( That is, the number of nodes passed by the fast pointer must be twice that of the slow pointer ) * f = s + nb ( When the two meet , Quick, the pointer must have gone around n circle ) * From the above two equations, we can get ,f = 2nb,s = nb * So we know , When two hands meet , The slow pointer has gone nb Step , It is known that we are going to the entry node , Need to go a + kb Step , And then s = nb Just go again a You can reach the entrance , Let's move the fast pointer * End node , Then the two pointers go back step by step , When they meet, the location is the entry node * step 1: The way to judge whether there are rings in the linked list is to judge whether there are rings in the linked list , And find the node that meets . * step 2: The slow pointer continues to meet the node , Quick pointer back to the chain header , The two pointers synchronously start to traverse the linked list element by element . * step 3: The place where we meet again is the entrance of the ring . **/
public class top7 {
// Judge if there is a ring , Return to where you met
public ListNode hasCycle(ListNode head) {
// First judge if the linked list is empty
if (head == null) return null;
// Fast slow double pointer
ListNode fast = head;
ListNode slow = head;
// If there is no ring, the fast pointer will go to the end of the list first
while (fast != null && fast.next != null) {
// Move the pointer two steps
fast = fast.next.next;
// Move the slow pointer one step
slow = slow.next;
// There is a ring when you meet , Return to where you met
if (fast == slow) return slow;
}
// To the end, there is no ring , return null
return null;
}
public ListNode EntryNodeOfLoop(ListNode pHead) {
ListNode slow = hasCycle(pHead);
// No ring
if (slow == null) return null;
// Quickly return the pointer to the meter
ListNode fast = pHead;
// Meeting again is the ring entrance
while (fast != slow) {
fast = fast.next;
slow = slow.next;
}
return slow;
}
}
TOP8 Last in the list k Nodes
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-EIjUVWpS-1658559347669)(D:\desktop\bite\mdpng\image-20220721161826089.png)]](/img/dc/2b7e5c80939b9694fecdef463a9f88.png)
/** * 8 Last in the list k Nodes * step 1: Prepare a quick pointer , From the head of the chain , Go first on the list k Step . * step 2: Prepare the slow pointer to point to the original chain header , Represents the current element , Then the distance between the slow pointer and the fast pointer is always k. * step 3: The speed pointer moves synchronously , When the fast pointer reaches the end of the list , The slow pointer just counts down k The location of the elements . **/
public class top8 {
public ListNode FindKthToTail (ListNode pHead, int k) {
ListNode fast = pHead;
ListNode slow = pHead;
// Let's go first K Step
for (int i = 0; i < k; i++) {
if (fast != null) fast = fast.next;
// It indicates that the length of the linked list is less than K
else return null;
}
// When the fast pointer is not empty , The speed pointer advances synchronously
while (fast != null) {
fast = fast.next;
slow = slow.next;
}
// The fast pointer is null , That's all , The slow pointer points to the penultimate k Location of nodes
return slow;
}
}
TOP9 Delete the last of the linked list n Nodes
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-uNMtshE5-1658559347670)(D:\desktop\bite\mdpng\image-20220721171635890.png)]](/img/13/95605d284b6c509d7f1564c8240f6a.png)
public class Solution {
/** * @param head ListNode class * @param n int integer * @return ListNode class */
public ListNode removeNthFromEnd (ListNode head, int n) {
// Add header , To save it , To prevent modification
// Return to the next node in the header
ListNode res = new ListNode(-1);
res.next = head;
ListNode pre = res;
ListNode fast = head;
ListNode slow = head;
// Let the fast pointer go forward first k Step
for(int i = 0; i < n ; i++) {
if(fast != null) fast = fast.next;
// It indicates that the length of the linked list is less than k
else return null;
}
while(fast != null) {
fast = fast.next;
pre = pre.next;
slow = slow.next;
}
// At this time, the fast pointer has reached null , The node pointed by the slow pointer is the node to be deleted
pre.next = slow.next;
return res.next;
}
}
TOP10 The first common node of two linked lists
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-2HyGWJTQ-1658559347670)(D:\desktop\bite\mdpng\image-20220722155607320.png)]](/img/47/050bfa2ea2fab1207a5e97d7d0c31a.png)
public class Solution {
public ListNode FindFirstCommonNode(ListNode pHead1, ListNode pHead2) {
// ListNode l1 = pHead1;
// ListNode l2 = pHead2;
// while(l1 != l2) {
// l1 = (l1 == null) ? pHead2 : l1.next;
// l2 = (l2 == null) ? pHead1 : l2.next;
// }
// return l1;
// Calculate the length of two linked lists
int len1 = length(pHead1);
int len2 = length(pHead2);
// If the length of two linked lists is different , Those with more nodes go first , Until they are the same length
while(len1 != len2) {
if(len1 > len2) {
pHead1 = pHead1.next;
len1 --;
}else {
pHead2 = pHead2.next;
len2 --;
}
}
// At this time, the length of the two linked lists is equal , Compare its element size
while(pHead1 != pHead2) {
pHead1 = pHead1.next;
pHead2 = pHead2.next;
}
// Go to the end , In the end, there are two possibilities , One is head1 It's empty ,
// In other words, they don't intersect . Another possibility is that head1
// Not empty , in other words head1 It's their intersection
return pHead1;
}
private int length(ListNode head) {
int n = 0;
while(head != null) {
head = head.next;
n++;
}
return n;
}
}
TOP11 Add the linked list ( Two )
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-SkJw7Pav-1658559347670)(D:\desktop\bite\mdpng\image-20220722165630295.png)]](/img/2c/f1260308d1cdfa89ef7d1920a1e38a.png)
public class Solution {
/** * @param head1 ListNode class * @param head2 ListNode class * @return ListNode class */
public ListNode addInList (ListNode head1, ListNode head2) {
if(head1 == null) return head2;
if(head2 == null) return head1;
ListNode l1 = reverse(head1);
ListNode l2 = reverse(head2);
ListNode res = null;
int c = 0; // carry
// If c > 0 Then it means that there is a carry and a node has to be inserted
while(l1 != null || l2 != null || c > 0) {
int v1 = l1 != null ? l1.val : 0;
int v2 = l2 != null ? l2.val : 0;
int total = v1 + v2 + c; // The sum of the current one
c = total / 10;
// Insert the current node
ListNode temp = new ListNode(total % 10); // Current bit
temp.next = res;
res = temp;
if(l1 != null) l1 = l1.next;
if(l2 != null) l2 = l2.next;
}
return res;
}
// Flip list
public ListNode reverse(ListNode head) {
if(head == null) return null;
ListNode pre = null;
while(head != null) {
ListNode next = head.next;
head.next = pre;
pre = head;
head = next;
}
return pre;
}
}
边栏推荐
- Learn NLP with Transformer (Chapter 1)
- MySQL | GROUP_CONCAT函数,将某一列的值用逗号拼接
- BGP联邦实验
- Druid 查询超时配置的探究 → DataSource 和 JdbcTemplate 的 queryTimeout 到底谁生效?
- 【域泛化】2022 IJCAI领域泛化教程报告
- HCIP (01)
- Openstack Skyline 组件安装
- The integration of two in one has a long way to go
- 【IJCAI 2022】参数高效的大模型稀疏训练方法,大幅减少稀疏训练所需资源
- C3d model pytorch source code sentence by sentence analysis (I)
猜你喜欢
随机推荐
【高并发】通过源码深度分析线程池中Worker线程的执行流程
HCIP(12)
【云享新鲜】社区周刊·Vol.72- 2022华为开发者大赛中国区首场开幕式启动;华为云KooMessage火热公测中…
JS hash table 01
Nb-iot control LCD (date setting and reading)
推荐系统-协同过滤在Spark中的实现
tensorflow 调用多块GPU的一些错误
史上最全的立创元器件封装库导入AD详细教程(一直白嫖一直爽)
Learn NLP with Transformer (Chapter 3)
ESP8266 使用 DRV8833驱动板驱动N20电机
MySQL | GROUP_CONCAT函数,将某一列的值用逗号拼接
Google Earth engine -- Statistics on the frequency of land classification year by year
最详细的mysql索引解析(文末附赠思维导图)
[flask advanced] solve the classic error reporting of flask by combining the source code: working outside of application context
[information system project manager] thought map series essence summary
Flask框架——消息闪现
C3d model pytorch source code sentence by sentence analysis (I)
HCIP(11)
SQL语言(三)
【Servlet】请求的解析