当前位置:网站首页>IP protocol - network segment division
IP protocol - network segment division
2022-07-24 15:29:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm your friend, Quan Jun .
IP Address
On the basis of TCP/IP When the protocol is communicating , Use IP Address to identify the host or router . stay IPv4 in ,IP The address is a 32 An integer . So the maximum number that can be represented IP The address is :2^32( It's about 43 Billion ).
IP The address is identified by network number and host number . Hosts in different network segments must have different network identities . The network number of the host in the same network segment means the same , But the host ID must be different . therefore , After adding a host in a network segment , The network number of the host is the same as that of the network segment , But the host number cannot be the same as that of other hosts in the network segment .
Through the reasonable setting of network number and host number , You can guarantee that in an interconnected network , For each host IP The address is unique .
There is a kind of DHCP technology , It can automatically assign the hosts of new nodes in the network segment IP Address . Most routers come with DHCP function , So a router can be seen as a DHCP The server .
By way of IP Address is divided into network number and host number to identify , It can have the following characteristics :
(1)IP Address management agencies are allocating IP Only the network number is assigned to the address . The remaining host number is assigned by the unit that gets the network number , In this way, the management is convenient, and the management is enough ;
(2) The router is looking for the destination host IP Address time , Just find the LAN where the destination host is located , Then look for the destination host in the LAN .
(3) LANs with different network numbers must be connected by routers , So routers always have two or more different network numbers IP Address
So how to divide network number and host number ?
IP Address classification
IP Addresses can be divided into five categories :A~E class . The network number and host number of each category are as follows :
The range of addresses is :
A class :0.0.0.0~127.255.255.255
B class :128.0.0.0~191.255.255.255
C class :192.0.0.0~223.255.255.255
D class :224.0.0.0~239.255.255.255
E class :240.0.0.0~247.255.255.255
A The network number of the class address occupies 1 Bytes , Only 7 Bits can be used . Can be assigned A Class network number is 126(2^7-2) individual .A class IP The network fields in the address are all 0 It means “ This network (A Class network )” It means , Not used to assign to specific hosts .IP All network numbers in the address 1 This is the local loopback address , Used to test the communication between the processes of the host , That is, the network number is 127 Of IP Address .A The host number of the class address occupies 3 Bytes , So a A The maximum number of hosts that can be connected in a class network is :2^24-2. The host number is full 0 Represents the single network address to which the host is connected ( Some A Class network ), The host number is full 1 Represents all hosts in the network .
B The network number of the class address occupies 2 Bytes , Only 14 Bits can be used . Can be assigned B Class network number is 2^14-1(128.0.0.0) no need , The minimum network number is :128.1.0.0. every last B The maximum number of hosts that can be connected to a class network is :2^16-2=65534.( Deduct the host number 0 And all 1 Of IP Address ).
C The network number of the class address occupies 3 Bytes , Only 21 Bits can be used . Can be assigned C Class network number is 2^21(192.0.0.0 no need ), The minimum network number is :192.0.1.0. every last C The maximum number of hosts that class hosts can connect to is :2^8-2=254( Deduct the host number for all 0 And all 1 Of IP Address ).
In the above classification , There are the following problems :
(1)IP Reduced utilization of address space : One B The most classes in a network can represent IP The address is 65534 individual , However, the number of nodes that can be connected to some kinds of networks is limited due to the characteristics of links , So there will be a lot of IP Address waste ; because C The number of nodes that a class network can connect is limited . therefore , Units will apply for B Class network , But you can't use so many IP Address , So it will cause IP Waste of address . Empathy ,A Network like IP Addresses can also cause a lot of waste ;
(2) If you assign a network number to each physical network , This will cause the routing table to be too large . This will increase the management cost of routing table , At the same time, the efficiency of query will also increase .
(3) When a unit applies for a network number . He wants to put what the network can express IP When the address is assigned to its subordinate units . If you're applying for a new network, it's a waste .
In order to solve the above problems , The concept of subnet partition is introduced .
Subnet partition and subnet mask
Subnet partition
Subnet partition is actually the original A class ,B class ,C The part of the host number in the class network is used as the subnet number , The original ABC The process of thinning the class network , Divide the original network into multiple networks , But in terms of external performance , Or the performance of the original network .
therefore , here ,IP The address consists of : network number + Subnet number + Host number .
In the process of data communication , First of all, according to the purpose IP Address find the network where the target host is located ( Router ), According to the purpose IP Address subnet number to find the subnet of the target host , Finally find the target host .
such as , One B class IP The address is :192.168.0.0. First divide the network into several subnets , Suppose the subnet number occupies 8 position . Because of the original B The host number in the class network occupies a total of 16 position , Subnet takes away 8 Bit after , The number of bits of host number in a subnet becomes 8 position . Suppose one of the subnets is 192.168.5.0. In data communication , The destination host is... In the subnet IP The address is 192.168.5.8 The host . therefore , In the process of data transmission , First, according to the purpose IP Address find the network where the host is located 192.168.0.0( In fact, it is to find the router on the network ), Re pass IP Address find the subnet where the destination host is located 192.168.5.0. Finally, find the destination host in the subnet .
here , Network number and subnet number can be unified as network identification .
Subnet mask
When the datagram reaches the router of the network where the destination host is located , How to forward it to the subnet ?
In order to make the router of the network where the destination host is located to find the destination subnet easily , introduce “ Subnet mask ” The concept of . The subnet mask is also a 32 An integer , It's made up of a string of 1 And a bunch of 0 constitute ,1 Corresponding to the network number and subnet number of the destination host ,0 Corresponding to the host number of the destination host . For the network number without subnet Division , There are also subnet masks , At this time, in the subnet mask 1 Corresponding to the network number ,0 Corresponding to the host number . Network number and subnet number are collectively referred to as network number , In the subnet mask 1 It corresponds to the network number ,0 Corresponding to the host number .
Will target the host's IP Address and subnet mask are bitwise and manipulated , You can determine the network number of the destination host .
Here's the picture :
here , The destination host IP After that, we get the address and destination of the network IP. In this case , The host of this subnet IP The representation range of is :145.13.3.0~145.13.3.255. The number of hosts that can be connected is 254 platform ( Remove the host number to all 0 And all 1 Of IP Address ).
Above mentioned , Subnet mask and host IP Bitwise and then get the network address , And then the host number will be all 0 all have arrived 1 That is, the address range of the subnet .
Subnet mask in addition to the above representation , There's another way to express it : At every IP Add the number of bits of the network address after the address . The above case, :
145.13.3.10/24. It means IP The address is 145.13.3.10 The host IP, High subnet mask 24 Bit is whole 1. So the network address is high 24 Position and should IP The same address is 145.13.3.0.
therefore , In the routing table, there must be a destination network address , Also have a subnet mask for the network . To judge the purpose IP Whether it corresponds to the destination network address .
special IP Address
With the above ABC Similar classes , The host number is all 0 It means “ The network ”, The host number is all 1 It means “ All hosts ” The broadcast address .127. The first one is the native loopback test , It's usually 127.0.0.1.
CIDR
because A Class has a limited number of network numbers that can be assigned , and C The number of hosts that can be connected to a class network is relatively small , So the general unit in the application network , Will apply for B Class network , And that leads to this B There is a serious lack of quasi networks .
therefore , Start giving up IP Classification of addresses , Divide by any length IP Network ID and host ID of address , It is associated with ABC The division of classes has nothing to do with . be called CIDR. It can be free from IP Restrictions on address classification , Free to distribute .
At this time IP The address can be expressed as : network number + Host number ( This network number can be of any length ).
When you apply for a network number of any length , You can also divide subnets within the network . So for any subnet, there is also a subnet mask . Use the same method as above .
CIDR More effective use of the current IPv4 Address , At the same time, it also reduces the burden of routers . It can combine multiple consecutive C Class addresses are merged into one network ( And your precious number 2,4,8,… present ). for example : Put two C Class network :192.168.224.0 and 192.168.225.0 Merge into one network . At this time, the number of hosts that can be connected in the merged network is increased to 2^9-2=510 platform . Before the merger , You need to occupy two rows in the routing table to represent two C Class network , After merging, it can be expressed in one line .
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/124749.html Link to the original text :https://javaforall.cn
边栏推荐
- 接参处理和@Param
- 力扣 31.下一个排列--双指针法
- Still using listview? Use animatedlist to make list elements move
- Sklearn.metrics module model evaluation function
- 你不能只会flex居中布局,精制动画讲解所有flex布局方式!通俗易懂纯干货教程!...
- Is it safe for Huatai Securities to open a mobile account and will it be leaked
- Getting started with mongodb
- 被攻击怎么解决?DDoS高防IP防护策略
- 2022 RoboCom 世界机器人开发者大赛-本科组(省赛)---第一题 不要浪费金币 (已完结)
- Join parameter processing and @param
猜你喜欢

Reentrantlock reentrant lock

celery 启动beat出现报错ERROR: Pidfile (celerybeat.pid) already exists.
报错【项目报错】
Performance test - analyze requirements

Use of keywords const, volatile and pointer; Assembly language and view of register status

(09) flask is OK if it has hands - cookies and sessions

24.原生磁盘的使用

2022 RoboCom 世界机器人开发者大赛-本科组(省赛)-- 第三题 跑团机器人 (已完结)

【TA-霜狼_may-《百人计划》】图形3.4 延迟渲染管线介绍

Analysis of some difficulties in VAE (variational self encoder)
随机推荐
YOLO5Face:为什么要重新发明人脸检测器
Huffman tree (optimal binary tree)
Jmeter-调用上传文件或图片接口
【AdaptiveAvgPool3d】pytorch教程
How do novices buy stocks for the first time? Which securities company is the best and safest to open an account
MySql函数
(零九)Flask有手就行——Cookie和Session
String application - calculate the longest true prefix of a string
Force button 31. Next arrangement -- double finger needling
Is it safe for Huatai Securities to open a mobile account and will it be leaked
2022 robocom world robot developer competition - undergraduate group (provincial competition) -- question 3 running team robot (finished)
[fluent -- layout] flow layout (flow and wrap)
Here comes the problem! Unplug the network cable for a few seconds and plug it back in. Does the original TCP connection still exist?
2022 RoboCom 世界机器人开发者大赛-本科组(省赛)-- 第二题 智能服药助手 (已完结)
PyTorch的自动求导
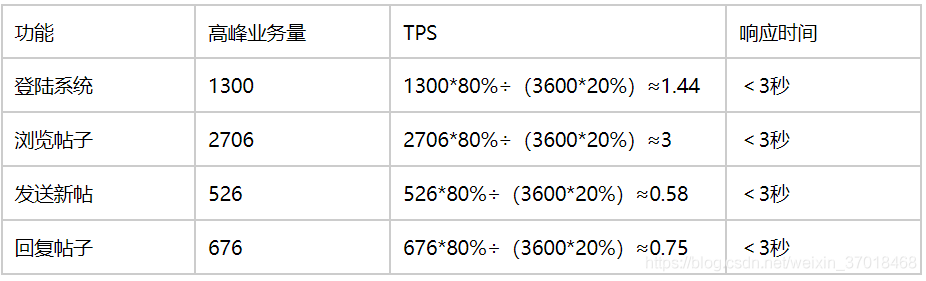
Performance test - analyze requirements
Circular structure practice
DS binary tree - maximum distance of binary tree nodes
Leetcode-09 (next rank + happy number + full rank)
2022 robocom world robot developer competition - undergraduate group (provincial competition) rc-u4 strategy team (completed)