当前位置:网站首页>C language advanced part III. string functions and memory operation functions
C language advanced part III. string functions and memory operation functions
2022-07-24 07:32:00 【And move forward with the high wind - & gt;】
Catalog
Memory manipulation function :
String function :
strlen
size_t strlen ( const char * str)
{
const char *eos = str;
while( *eos++ ) ;
return( eos - str - 1 );
}
strcpy
char* strcpy(char* const destination,char const*source)
{
char* des = destination;
while ((*destination++ = *source++) != '\0') { }
return des;
}strcat
Prototype :char * strcat ( char * destination, const char * source );
String append function , Realization :
char * strcat (char * dst,const char * src)
{
char * cp = dst;
while( *cp )
cp++; /* find end of dst */
while((*cp++ = *src++) != '\0') ; /* Copy src to end of dst */
return( dst ); /* return dst */
}Find the destination string first ‘\0’ And then from ‘\0’ Start appending to the source string ‘\0’ Also copy the past , so The target space must be large enough , It can hold the contents of the source string . The target space must be modifiable . The source string must be in '\0' end .
strcmp
int strcmp ( const char * str1, const char * str2 );
Compare the characters of two strings in turn ASCII Code value , The return value is specified as follows :
The standard stipulates :
The first string is larger than the second string , Return greater than 0 The number of
The first string is equal to the second string , Then return to 0
int strcmp (const char * src, const char * dst)
{
int ret = 0 ;
while((ret = *(unsigned char *)src - *(unsigned char *)dst) == 0 && *dst)
{
++src, ++dst;
}
return ((-ret) < 0) - (ret < 0); // (if positive) - (if negative) generates
//branchless code
// Limit the return value to 0,1,-1
}strncpy
char * strncpy ( char * destination, const char * source, size_t num );
strncat
char * strncat ( char * destination, const char * source, size_t num );
strncmp
int strncmp ( const char * str1, const char * str2, size_t num );
Similar to the above string function with limited length , But there is one more parameter num : The number of characters , You can specify the number of characters for the operation .
strstr
A function that finds a substring in a parent string , Will return the character pointer of the first substring found .
Function implementation :( The original method finds the substring , Than KMP,sunday And other algorithms are inefficient )
From a string str1 Find string in str2
char * strstr (const char * str1,const char * str2)
{
char *cp = (char *) str1;
char *s1, *s2;
if ( !*str2 ) Substring str2 It's empty , Return parent string
return((char *)str1);
while (*cp)
{
s1 = cp; String pointer
s2 = (char *) str2; Substring pointer
while ( *s2 && !(*s1-*s2) )
s1++, s2++;
if (!*s2) If the substring pointer points to ‘\0’, Find success , Return the corresponding parent string position
return(cp);
cp++;
}
return(NULL);
}
String cutting function
strtok
Prototype :![]()
For example, two strings :
char string[] = "A string\tof ,,tokens\nand some more tokens";
char seps[] = " ,\t\n";
Usage method
printf( "%s\n\nTokens:\n", string );
/* Establish string and get the first token: */
token = strtok( string, seps );
while( token != NULL )
{
/* While there are tokens in "string" */
printf( " %s\n", token );
/* Get next token: */
token = strtok( NULL, seps );// Pass in NULL, The function will start from last '\0' Start cutting at the back
}
After each cutting with this function, this function will return the address before cutting , And modify the original string cutting character to '\0', The next cut will be from ‘\0’ Start , In this way, you will get
A
string
of
tokens
and
some
more
tokens
strerror

Pass in the error code errno, This function returns the first address of the error message string , Used to print error messages
![]()
Memory manipulation function :
memcpy
Memory copy function , Definition :

memmove
And memcpy similar , But it's more powerful , Can achieve destination and source Overlapping copies , Because function implementations are copied from overlapping areas .
Simulation Implementation

memcmp
Compare two memory areas byte by byte , similar strcmp The function compares the corresponding data ASCII Code value .
Realization :
int memcmp(char* buf1,char *buf2,unsigned count)
{
if (!count)
return(0);
while (--count && *buf1 == *buf2)
{
buf1++;
buf2++;
}
return(*buf1 - *buf2);
}边栏推荐
- Stm32h750vbt6 drives programmable gain amplifier module pga113 -- Hal Library Based on cubemx
- Riotboard development board series notes (IX) -- buildreoot porting matchbox
- Oauth2==sso three protocols. Oauth2 four modes
- Gimp custom screenshot
- UNI-APP_小程序或h5页面背景音乐的播放与暂停
- 从CIA看常见网络攻击(爆破,PE,流量攻击)
- 剑指offer专项突击版第8天
- 全国职业院校技能大赛网络安全B模块 Windows操作系统渗透测试
- Nacos的高级部分
- [hiflow] Tencent cloud hiflow scene connector realizes intelligent campus information management
猜你喜欢

Bookkeeping app: xiaoha bookkeeping 2 - production of registration page

爬虫学习-概述

Jackson 解析 JSON 详细教程

Vulnhub DC1

全国职业院校技能大赛网络安全B模块 缓冲区溢出漏洞

从CIA看常见网络攻击(爆破,PE,流量攻击)
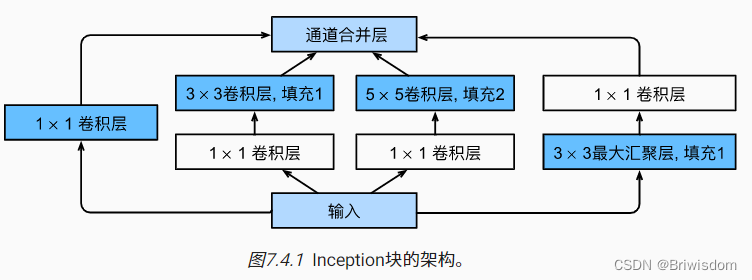
Deep learning two or three things - review those classical convolutional neural networks

Service Vulnerability & FTP & RDP & SSH & Rsync
Who can stand it when the project goes online

Influxdb unauthorized access & CouchDB permission bypass
随机推荐
[steering wheel] code review ability of idea to ensure code quality
JS_ Realize the separation of multiple lines of text into an array according to the newline
Kali installing PIP and pip source changing
剑指offer专项突击版第8天
Influxdb unauthorized access & CouchDB permission bypass
MITRE ATT&CK超详细学习笔记-02(大量案例)
Requests crawler multi page crawling to KFC restaurant location
Deep learning two or three things - review those classical convolutional neural networks
二维平面多段线Y轴最短距离
nacos配置中心源码分析
Paper reading: hardnet: a low memory traffic network
【信息系统项目管理师】第七章 复盘成本管理知识架构
baddy:核心函数入口
Jackson 解析 JSON 详细教程
Customization or GM, what is the future development trend of SaaS in China?
The goal you specified requires a project to execute but there is no POM in this directory
Chapter007 FPGA learning IIC bus EEPROM reading
File upload and download demo
oracle中有A,B连个表,这两个表需要第三个表C关联,那怎么将A表中的字段MJ1更新为B表中MJ2的值
Seminar 2022.07.22 -- Comparative learning