当前位置:网站首页>Jenkins pipeline uses
Jenkins pipeline uses
2022-06-25 12:52:00 【kunwen123】
Jenkins Pipeline Use
https://www.linux-note.cn/?p=491
边栏推荐
- Array reorder based on a field
- The push(), pop(), unshift(), shift() method in the JS array
- 3+1 guarantee: how is the stability of the highly available system refined?
- laravel 9
- Meichuang was selected into the list of "2022 CCIA top 50 Chinese network security competitiveness"
- 模块五(微博评论)
- (4) Pyqt5 tutorial -- > Custom signal and slot (super winding...)
- Event triggered when El select Clear clears content
- Flutter automatically disappears after receiving push
- Connect with the flight book and obtain the user information according to the userid
猜你喜欢
![[data visualization] 360 ° teaching you how to comprehensively learn visualization - Part 1](/img/36/167397ce61240036c865dd99463f1b.jpg)
[data visualization] 360 ° teaching you how to comprehensively learn visualization - Part 1

出手即不凡,这很 Oracle!

顺序表的折半查找法

2021-10-21

(3) Pyqt5 tutorial -- > signal and slot preliminary test

地理空间搜索 ->R树索引
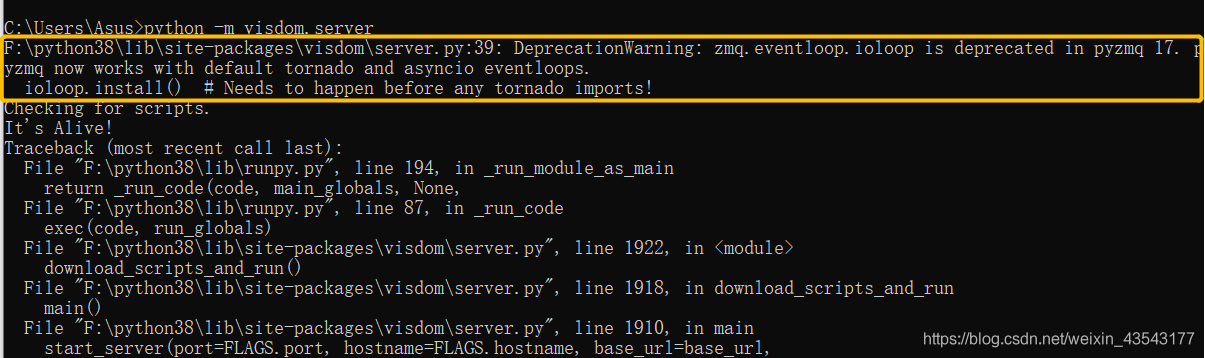
Another night when visdom crashed

GNSS receiver technology and application review

MySQL writes user-defined functions and stored procedure syntax (a detailed case is attached, and the problem has been solved: errors are reported when running user-defined functions, and errors are r
模块五(微博评论)
随机推荐
Shell learning notes (latest update: 2022-02-18)
(5) Pyqt5 ---- another method of connecting signals and slots
Figure explanation of fiborache sequence
Concat(), join(), reverse(), sort() method in JS array
Maximum number [abstract rules for abstract sorting]
JS enter three integers a, B and C, and sort them from large to small (two methods)
20220620 面试复盘
最大数[抽象排序之抽象规则]
Baidu search stability analysis story
Possible problems when idea encounters errors occurred while compiling module (solved)
PPT绘图之AI助力论文图
Total number of MySQL statistics, used and unused
Micro engine remote attachment 7 Niu cloud upload
三入职场!你可以从我身上学到这些(附毕业Vlog)
20220620 interview reply
Zhangxiaobai's way of penetration (III) -- detailed explanation of SQL injection vulnerability principle (SQL Server)
二叉树之_哈夫曼树_哈弗曼编码
GPS receiver design (1)
Possible causes of wechat applet decryption failure
Geospatial search: implementation principle of KD tree
