当前位置:网站首页>Sentinel flow control quick start
Sentinel flow control quick start
2022-07-24 10:31:00 【Liu Chu, Ge Nian】
List of articles
flow control
Although there are four solutions to the avalanche problem , However, current limiting is to avoid service failure due to sudden traffic , It is the prevention of the avalanche of microservices .
Can prevent the best , So let's first introduce flow control :
1. Cluster link
When requesting access to the microservice , First of all, I will visit DispatcherServlet( Front controller ), Then enter Controller、Service、Mapper, Such a call chain is called cluster [cù] Point link .
Each monitored interface in the cluster link is a resources .
By default sentinel Will monitor SpringMVC Every endpoint of (Endpoint, That is to say controller The method in ), therefore SpringMVC Every endpoint of (Endpoint) Is to call a resource in the link .
Small expansion :DispatcherServlet It's the front controller , Configure in web.xml In the document . Block matching requests ,Servlet The interception matching rules should be defined by themselves , Put the intercepted request , Distribute to the target... According to the corresponding rules Controller To deal with it , It's configuration spring MVC The first step .
DispatcherServlet It is the implementation of the design pattern of the front-end controller , Provide Spring Web MVC The central access point of , And responsible for the assignment of responsibilities , And with the Spring IoC Seamless integration of containers , So that you can get Spring All the benefits of .
for example , We visited order-service Medium OrderController Endpoint in :/order/{orderId}
stay Sentinel There will be a display in the console ( No first visit , The request will not be displayed here )
Flow control 、 Fusing, etc. are set for the resources in the cluster link , Therefore, we can click the button behind the corresponding resource to set the rules :
| The rules | explain |
|---|---|
| Flow control | flow control |
| Downgrade | Degraded fuse |
| hotspot | Hot spot parameter current limiting , It is a kind of current limiting |
| to grant authorization | Request permission control |
Let's start with a quick start , Then explain the configuration of each rule in detail
2. Quick start
2.1. Example
Click resources /order/{orderId} The flow control button at the back , You can pop up a form .

Flow restriction rules can be filled in the form , as follows :

It means to limit /order/{orderId} The stand-alone of this resource QPS by 1, That is, only 1 Requests , The exceeded request will be intercepted and an error will be reported .

If we ask too soon , He will control the flow , Show the access , For example, visit the browser with your life , It will return an error message

2.2. practice :
demand : to /order/{orderId} This resource sets flow control rules ,QPS No more than 5, Then test .
1) First, in the sentinel Add current limit rule to console

2) utilize jmeter test
Turn on 20 Thread access 20 Time
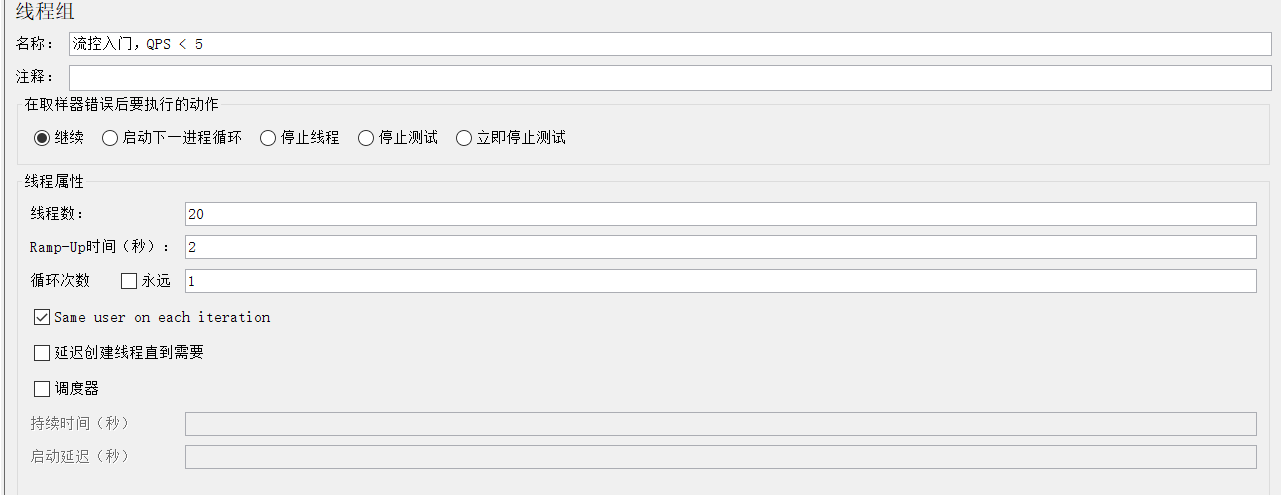
Set request information

20 Users ,2 Run... In seconds ,QPS yes 10, More than the 5.
Run the test
Be careful , Do not click the execute button in the menu to run .
result :

You can see , Successful requests only... At a time 5 individual
边栏推荐
猜你喜欢

NIO知识点

Implementation and traversal of binary tree and binary tree sorting tree

Ribbon's loadbalancerclient, zoneawareloadbalancer and zoneavoidancerule are three musketeers by default

The paper of gaojingjian center was selected into the ACL 2022 of the international summit to further expand the privacy computing capacity of Chang'an chain
MySQL - 全文索引

Association Rules -- July 10, 2022

How to solve the problem of robot positioning and navigation in large indoor scenes with low-cost solutions?

WEB安全基础 - - -文件上传(文件上传绕过)

Analysis of Kube proxy IPVS mode

Constant pointer, pointer constant
随机推荐
Analysis of distributed lock redistribution principle
Sentinel 三种流控模式
Configuration description and componentization development steps of various documents in the scaffold
Mysql InnoDB下联合索引的索引数量?
Will not be rejected! Learn the distributed architecture notes sorted out by Alibaba Daniel in 35 days, with a salary increase of 20K
Google cooperates with colleges and universities to develop a general model, proteogan, which can design and generate proteins with new functions
图像处理:浮点数转定点数
String__
Ffmpeg splash screen solution (modify the source code and discard incomplete frames)
The method modified by private can be accessed through reflection. What is the meaning of private?
MySQL - 索引的隐藏和删除
Nirvana rebirth! Byte Daniel recommends a large distributed manual, and the Phoenix architecture makes you become a God in fire
The paper of gaojingjian center was selected into the ACL 2022 of the international summit to further expand the privacy computing capacity of Chang'an chain
zoj-Swordfish-2022-5-6
关联规则--2022年7月10日
Add a love power logo to your website
差分约束系统---1且2--2022年5月27日
Balance between management / business and technology
fatal: unable to commit credential store: Device or resource busy
Chapter V Modification implementation (impl) class