当前位置:网站首页>Security policy and NAT (easy IP) of firewall Foundation
Security policy and NAT (easy IP) of firewall Foundation
2022-06-22 20:16:00 【51CTO】
Firewall deployment security policy and NAT
Principle overview :
Easy IP It is a kind of public network using outgoing interface IP Address as NAT Post transfer address , Address conversion method for converting addresses and ports at the same time , For interfaces IP Is a dynamically acquired scene ,Easy IP Also support
When the public network interface of Huawei firewall dynamically obtains the public network address through dialing , If you only want to use this public network IP Address to address translation , Not at this time NAT Configure fixed addresses in the address pool , Because the public network IP The address changes dynamically , here , have access to Easy IP The way , Even if the public network obtained on the outgoing interface IP The address has changed , Huawei firewall will also follow the new public network IP Address to address translation
When the host passes through Easy IP visit Web Server when , The process of Huawei firewall is as follows
After Huawei firewall receives the message sent by the host , According to the purpose IP The address determination message needs to be in Trust Areas and Untrust Flow between regions , Find through security policy check follow-up NAT Strategy , It is found that address translation is required for the message
Huawei firewall usage and Internet The public network of the connected interface IP The source of the address replacement message IP Address , At the same time, replace the source port number of the message with the new port number , And create a conversation table , Then send the message to Internet
Huawei firewall received Web Server After responding to the message from the host , Match to step... By looking up the session table 2 Table entries created in , Replace the destination address of the message with that of the host IP Address , Replace the destination port number of the message with the original port number , Then send the message to Intranet
In this way , Because the address conversion is also carried out at the same time as the port conversion , Multiple private network users can use a public network IP Address online , Huawei firewall distinguishes different users according to ports , Therefore, the number of users who can access the Internet at the same time is more
A firewall ( English :Firewall) Technology is through the organic combination of all kinds of software and hardware equipment for safety management and screening , Help the computer network in it 、 Build a relatively isolated protective barrier between the external networks , A technology to protect user data and information security .
The function of firewall technology is to discover and deal with the possible security risks when the computer network is running 、 Data transmission and so on , The treatment measures include isolation and protection , At the same time, it can record and test all operations in computer network security , To ensure the security of computer network operation , Guarantee the integrity of user data and information , Better for users 、 More secure computer network experience .
So-called “ A firewall ” It refers to an intranet and public access network ( Such as Internet) The way of separation , It is actually an applied security technology based on modern communication network technology and information security technology , Isolation technology . It is more and more used in the interconnection environment of private network and public network , Especially with access Internet The Internet is the most important .
Firewall is a protective barrier between the internal and external network environment with the help of hardware and software , So as to block the unsafe network factors of the computer . Only with the consent of the firewall , Users can enter the computer , If you don't agree, you'll be blocked out , The alarm function of firewall technology is very powerful , When an external user wants to enter the computer , The firewall will quickly send out the corresponding alarm , And remind users of their behavior , And make self judgment to decide whether to allow external users to enter the interior , As long as the user is in the network environment , This kind of firewall can carry out effective query , At the same time, the information found will be displayed to the user , Then users need to implement corresponding settings for the firewall according to their own needs , Block the disallowed user behavior . Through the firewall, you can also effectively view the traffic of information data , And it can also master the speed of uploading and downloading data information , It is convenient for users to have good control judgment on the use of computers , The internal situation of the computer can also be viewed through this firewall , It also has the function of starting and closing the program , And the internal log function of the computer system , In fact, it is also a summary of the real-time situation of the firewall and the internal security of the computer system .
Firewall is a kind of access control scale which is executed when two networks communicate , It can prevent hackers from accessing your network to the maximum extent . It's set up on different networks ( Such as trusted intranet and untrusted public network ) Or a combination of components between network security domains . It is the only access to information between different networks or network security domains , Be able to control according to the safety policy of the enterprise ( allow 、 Refuse 、 monitoring ) Information flow in and out of the network , And it has strong anti attack ability . It's about providing information security services , Infrastructure for network and information security . Logically , The firewall is a separator , A limiter , It's also an analyzer , Effectively monitored the intranet and Internet Any activity between , Ensure the security of the internal network .
The firewall scans its network traffic , This will filter out some attacks , In case it is executed on the target computer . Firewalls can also shut down unused ports . And it can also disable outgoing traffic on specific ports , Block the Trojan horse . Last , It can disable access from special sites , To prevent all communications from unknown intruders .
The barrier of network security
A firewall ( As a blocking point 、 The control points ) It can greatly improve the security of an internal network , And reduce risk by filtering unsafe Services . Because only carefully selected application protocols can pass through the firewall , So the network environment becomes more secure . For example, firewalls can prohibit such as well-known unsafe NFS Protocol access to protected network , In this way, it is impossible for external attackers to use these fragile protocols to attack the internal network . Firewalls can also protect the network from routing based attacks , Such as IP Source routing attacks and ICMP Redirection path in redirection . The firewall should be able to reject all messages of the above types of attacks and notify the firewall administrator .
Strengthen network security strategy
Configure through a firewall centric security scheme , All security software ( Like a password 、 encryption 、 Identity Authentication 、 Audit, etc ) Configure on the firewall . Compared with dispersing network security issues to various hosts , Centralized security management of firewall is more economical . For example, during network access , The one-time password system and other identity authentication systems do not have to be scattered on each host , And focus on the firewall .
Monitoring audit
If all access passes through the firewall , that , The firewall can record these accesses and log them , At the same time, it can also provide statistical data of network usage . When something suspicious happens , The firewall can give appropriate alarm , And provide detailed information on whether the network is monitored and attacked . in addition , It is also very important to collect the usage and misuse of a network . The first reason is to know whether the firewall can resist the detection and attack of attackers , And know whether the control of firewall is sufficient . Network usage statistics are also very important for network demand analysis and threat analysis .
Prevent the leakage of internal information
By using firewall to divide the internal network , It can realize the isolation of key network segments of intranet , Thus, the impact of local key or sensitive network security issues on the global network is limited . also , Privacy is an issue of great concern to the intranet , An unnoticed detail in an internal network may contain clues about security and attract the interest of external attackers , Some security vulnerabilities of the internal network have even been exposed . Using a firewall, you can hide those internal details, such as Finger,DNS Etc .Finger Displays the registered names of all users of the host 、 real name , Last login time and use shell Type, etc . however Finger The information displayed is very easy for attackers to learn . An attacker can know how often a system is used , Whether there are users connecting to the Internet in this system , Whether the system is noticed when being attacked, etc . Firewalls can also block information about internal networks DNS Information , The domain name of such a host and IP The address will not be known to the outside world . In addition to safety , The firewall also supports Internet Service enterprise internal network technology system VPN( Virtual private network ).
Logging and event notification
All data entering and leaving the network must pass through the firewall , The firewall records it through logs , It can provide detailed statistical information of network use . When a suspicious event occurs , The firewall can alarm and notify according to the mechanism , Provide information on whether the network is threatened .
The experiment purpose :
Realize mutual visits between branches and use the public network IP
The topology :

Basic configuration :
FW1:
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.2.20 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 20.0.0.10 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.

FW2:
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.3.10 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 30.0.0.20 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.

The security policy :
FW1:
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
security-policy
rule name acl1
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action permit
rule name acl2
source-zone untrust
destination-zone trust
destination-address 192.168.1.0 mask 255.255.255.0
service ftp
action permit
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.


FW2:
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2
#
security-policy
rule name acl1
source-zone trust
destination-zone untrust
source-address 192.168.4.0 mask 255.255.255.0
action permit
rule name acl2
source-zone untrust
destination-zone trust
destination-address 192.168.4.0 mask 255.255.255.0
service ftp
action permit
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.


NAT Deploy :
FW1:

FW2:

Configure the default route :
FW1:

FW2:

Configure router :
R1:

R2:

R3:
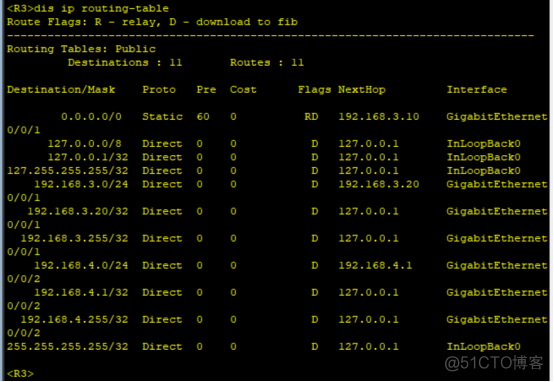
When the configuration is complete , Validation experiment


FW1:


FW2:


End of experiment ;
remarks : If there is a mistake , Please understand !
This article is my study notes , For reference only ! If there is a repetition !!! Please contact me
边栏推荐
- What can the accelerated implementation of digital economy bring to SMEs?
- 三维天地助力实验室夯实完整质量体系管理
- socket的connect函数用法
- ROS从入门到精通(八) 常用传感器与消息数据
- 图的存储结构(邻接矩阵)
- 51万奖池邀你参战!第二届阿里云ECS CloudBuild开发者大赛来袭
- Merge sort (recursive and iterative Implementation)
- 请你描述下从浏览器上输入一个url到呈现出页面的整个过程。
- 数字经济加速落地,能为中小企业带来什么?
- Connect function usage of socket
猜你喜欢
![[deeply understand tcapulusdb technology] view the online operation of tcapulusdb](/img/6f/2d62030e631e3085acf72951f2416f.png)
[deeply understand tcapulusdb technology] view the online operation of tcapulusdb

图的存储结构(邻接矩阵)

Traversal of trees and forests

如何低成本快速搭建企业知识库?

Matplotlib set axis scale interval

What can the accelerated implementation of digital economy bring to SMEs?
元宇宙中的云计算,提升你的数字体验

IVX no code challenge five second game production

防火墙基础之安全策略和NAT(Easy IP)

matplotlib设置坐标轴刻度间隔
随机推荐
Pit of undefined reference
IVX no code challenge five second game production
An error is reported when idea writes JSP code, but it is solved by normal operation
完全背包如何考慮排列問題
Merge sort (recursive and iterative Implementation)
【深入理解TcaplusDB技术】入门MySQL Driver
运用span-method巧妙实现多层table数据的行合并
【深入理解TcaplusDB技术】TcaplusDB新增机型
【深入理解TcaplusDB知识库】部署TcaplusDB Local版常见问题
[in depth understanding of tcapulusdb technology] getting started with MySQL driver
Gossip about redis source code 121
Implementation of balanced binary tree with C language
金鱼哥RHCA回忆录:DO447管理用户和团队的访问--创建和管理Ansible Tower用户
如何低成本快速搭建企业知识库?
Metu stability and operation and maintenance guarantee scheme
IDEA写jsp代码报错,但是正常运行解决
[deeply understand tcapulusdb technology] tcapulusdb table management - rebuild table
Shell Sort
Redis持久化的几种方式——深入解析RDB
[in depth understanding of tcapulusdb technology] introduction tcapulusdb problem summary