当前位置:网站首页>Debugged PEB (beingdebugged, ntglobalflag)
Debugged PEB (beingdebugged, ntglobalflag)
2022-07-25 20:50:00 【51CTO】
Ginger ginger ··················· ~!

As the title ,PEB In fact, there are many members that can be used to detect the debugger ( Although some of the original intention is not necessarily , But there will be fixed changes when being debugged ), But in Win7 after , There are only two that can be used :( So is this a good thing or a bad thing )
Both of the above come from _PEB Structure :( Here is 32 position ,64 We'll talk about it later )
typedef
struct
_PEB {
// Size: 0x1D8
/*000*/
UCHAR
InheritedAddressSpace;
/*001*/
UCHAR
ReadImageFileExecOptions;
/*002*/
UCHAR
BeingDebugged;
// When there is no debugger = 0, When there is a debugger = 1
/*003*/
UCHAR
SpareBool;
/*004*/
HANDLE
Mutant;
/*008*/
HINSTANCE
ImageBaseAddress;
/*00C*/
VOID
*
DllList;
/*010*/
PPROCESS_PARAMETERS
*
ProcessParameters;
/*014*/
ULONG
SubSystemData;
/*018*/
HANDLE
DefaultHeap;
/*01C*/
KSPIN_LOCK
FastPebLock;
/*020*/
ULONG
FastPebLockRoutine;
/*024*/
ULONG
FastPebUnlockRoutine;
/*028*/
ULONG
EnvironmentUpdateCount;
/*02C*/
ULONG
KernelCallbackTable;
/*030*/
LARGE_INTEGER
SystemReserved;
/*038*/
ULONG
FreeList;
/*03C*/
ULONG
TlsExpansionCounter;
/*040*/
ULONG
TlsBitmap;
/*044*/
LARGE_INTEGER
TlsBitmapBits;
/*04C*/
ULONG
ReadOnlySharedMemoryBase;
/*050*/
ULONG
ReadOnlySharedMemoryHeap;
/*054*/
ULONG
ReadOnlyStaticServerData;
/*058*/
ULONG
AnsiCodePageData;
/*05C*/
ULONG
OemCodePageData;
/*060*/
ULONG
UnicodeCaseTableData;
/*064*/
ULONG
NumberOfProcessors;
/*068*/
LARGE_INTEGER
NtGlobalFlag;
// When there is a debugger, it will be assigned 70h = 112
/*070*/
LARGE_INTEGER
CriticalSectionTimeout;
/*078*/
ULONG
HeapSegmentReserve;
/*07C*/
ULONG
HeapSegmentCommit;
/*080*/
ULONG
HeapDeCommitTotalFreeThreshold;
/*084*/
ULONG
HeapDeCommitFreeBlockThreshold;
/*088*/
ULONG
NumberOfHeaps;
/*08C*/
ULONG
MaximumNumberOfHeaps;
/*090*/
ULONG
ProcessHeaps;
/*094*/
ULONG
GdiSharedHandleTable;
/*098*/
ULONG
ProcessStarterHelper;
/*09C*/
ULONG
GdiDCAttributeList;
/*0A0*/
KSPIN_LOCK
LoaderLock;
/*0A4*/
ULONG
OSMajorVersion;
/*0A8*/
ULONG
OSMinorVersion;
/*0AC*/
USHORT
OSBuildNumber;
/*0AE*/
USHORT
OSCSDVersion;
/*0B0*/
ULONG
OSPlatformId;
/*0B4*/
ULONG
ImageSubsystem;
/*0B8*/
ULONG
ImageSubsystemMajorVersion;
/*0BC*/
ULONG
ImageSubsystemMinorVersion;
/*0C0*/
ULONG
ImageProcessAffinityMask;
/*0C4*/
ULONG
GdiHandleBuffer[
0x22];
/*14C*/
ULONG
PostProcessInitRoutine;
/*150*/
ULONG
TlsExpansionBitmap;
/*154*/
UCHAR
TlsExpansionBitmapBits[
0x80];
/*1D4*/
ULONG
SessionId;
}
PEB,
*
PPEB;
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
- 55.
- 56.
Anti debug code :
#pragma
void
*
PEB(){
void
*
Peb
=
NULL;
// receive _PEB Structure address
__asm
{
mov
eax,
fs:[
0x30] ;
PEB
mov
Peb,
eax
}
return
Peb;
}
bool
PEB_BegingDebugged(){
bool
BegingDebugged
=
false;
__asm
{
mov
eax,
fs:[
0x30] ;
PEB
mov
al,
byte
ptr
ds:[
eax
+
0x2] ;
BegingDebugged
stay
_PEB
Offset in
mov
BegingDebugged,
al
}
return
BegingDebugged;
}
bool
PEB_NtGlobalFlag(){
bool
NtGlobalFlag
=
NULL;
__asm
{
mov
eax,
fs:[
0x30] ;
PEB
mov
al,
byte
ptr
ds:[
eax
+
0x68] ;
NtGlobalFlag
stay
_PEB
Offset in
mov
NtGlobalFlag,
al
}
return
NtGlobalFlag;
}
#pragma
int
_tmain(
int
argc,
_TCHAR
*
argv[])
{
// Print PEB Initial address ( For reference )
std::
cout
<<
"PEB() = "
<<
PEB()
<<
std::
endl;
// Detect debugger
if(
PEB_BegingDebugged()){
MessageBox(
NULL,
"PEB_BegingDebugged() Found debugger , Program exit ",
"LYSM",
NULL);
ExitProcess(
0);
}
if((
int)
PEB_NtGlobalFlag()
==
112){
MessageBox(
NULL,
"PEB_NtGlobalFlag() Found debugger , Program exit ",
"LYSM",
NULL);
ExitProcess(
0);
}
// bypass A sign of success
MessageBox(
NULL,
" The program runs here ",
"LYSM",
NULL);
getchar();
return
0;
}
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
- 55.
- 56.
- 57.
- 58.
- 59.
- 60.
- 61.
- 62.
- 63.
- 64.
- 65.
- 66.
- 67.
The general function is :
Normal operation popup “ The program runs here ” Dialog box

Single out when being debugged “ Debugger detected ” And finish running

Be careful : Experiment with the original OD It works
Let's talk about it x64 Under the _PEB structure :
( This is win7x64 Next use windbg View local PEB structure )
lkd
>
dt
!
_PEB
nt
!
_PEB
+
0x000
InheritedAddressSpace :
UChar
+
0x001
ReadImageFileExecOptions :
UChar
+
0x002
BeingDebugged :
UChar
// BeingDebugged The offset does not change
+
0x003
BitField :
UChar
+
0x003
ImageUsesLargePages :
Pos
0,
1
Bit
+
0x003
IsProtectedProcess :
Pos
1,
1
Bit
+
0x003
IsLegacyProcess :
Pos
2,
1
Bit
+
0x003
IsImageDynamicallyRelocated :
Pos
3,
1
Bit
+
0x003
SkipPatchingUser32Forwarders :
Pos
4,
1
Bit
+
0x003
SpareBits :
Pos
5,
3
Bits
+
0x008
Mutant :
Ptr64
Void
+
0x010
ImageBaseAddress :
Ptr64
Void
+
0x018
Ldr :
Ptr64
_PEB_LDR_DATA
+
0x020
ProcessParameters :
Ptr64
_RTL_USER_PROCESS_PARAMETERS
+
0x028
SubSystemData :
Ptr64
Void
+
0x030
ProcessHeap :
Ptr64
Void
+
0x038
FastPebLock :
Ptr64
_RTL_CRITICAL_SECTION
+
0x040
AtlThunkSListPtr :
Ptr64
Void
+
0x048
IFEOKey :
Ptr64
Void
+
0x050
CrossProcessFlags :
Uint4B
+
0x050
ProcessInJob :
Pos
0,
1
Bit
+
0x050
ProcessInitializing :
Pos
1,
1
Bit
+
0x050
ProcessUsingVEH :
Pos
2,
1
Bit
+
0x050
ProcessUsingVCH :
Pos
3,
1
Bit
+
0x050
ProcessUsingFTH :
Pos
4,
1
Bit
+
0x050
ReservedBits0 :
Pos
5,
27
Bits
+
0x058
KernelCallbackTable :
Ptr64
Void
+
0x058
UserSharedInfoPtr :
Ptr64
Void
+
0x060
SystemReserved : [
1]
Uint4B
+
0x064
AtlThunkSListPtr32 :
Uint4B
+
0x068
ApiSetMap :
Ptr64
Void
+
0x070
TlsExpansionCounter :
Uint4B
+
0x078
TlsBitmap :
Ptr64
Void
+
0x080
TlsBitmapBits : [
2]
Uint4B
+
0x088
ReadOnlySharedMemoryBase :
Ptr64
Void
+
0x090
HotpatchInformation :
Ptr64
Void
+
0x098
ReadOnlyStaticServerData :
Ptr64
Ptr64
Void
+
0x0a0
AnsiCodePageData :
Ptr64
Void
+
0x0a8
OemCodePageData :
Ptr64
Void
+
0x0b0
UnicodeCaseTableData :
Ptr64
Void
+
0x0b8
NumberOfProcessors :
Uint4B
+
0x0bc
NtGlobalFlag :
Uint4B
// NtGlobalFlag Offset by 0x68 → 0xbc
+
0x0c0
CriticalSectionTimeout :
_LARGE_INTEGER
+
0x0c8
HeapSegmentReserve :
Uint8B
+
0x0d0
HeapSegmentCommit :
Uint8B
+
0x0d8
HeapDeCommitTotalFreeThreshold :
Uint8B
+
0x0e0
HeapDeCommitFreeBlockThreshold :
Uint8B
+
0x0e8
NumberOfHeaps :
Uint4B
+
0x0ec
MaximumNumberOfHeaps :
Uint4B
+
0x0f0
ProcessHeaps :
Ptr64
Ptr64
Void
+
0x0f8
GdiSharedHandleTable :
Ptr64
Void
+
0x100
ProcessStarterHelper :
Ptr64
Void
+
0x108
GdiDCAttributeList :
Uint4B
+
0x110
LoaderLock :
Ptr64
_RTL_CRITICAL_SECTION
+
0x118
OSMajorVersion :
Uint4B
+
0x11c
OSMinorVersion :
Uint4B
+
0x120
OSBuildNumber :
Uint2B
+
0x122
OSCSDVersion :
Uint2B
+
0x124
OSPlatformId :
Uint4B
+
0x128
ImageSubsystem :
Uint4B
+
0x12c
ImageSubsystemMajorVersion :
Uint4B
+
0x130
ImageSubsystemMinorVersion :
Uint4B
+
0x138
ActiveProcessAffinityMask :
Uint8B
+
0x140
GdiHandleBuffer : [
60]
Uint4B
+
0x230
PostProcessInitRoutine :
Ptr64
Void
+
0x238
TlsExpansionBitmap :
Ptr64
Void
+
0x240
TlsExpansionBitmapBits : [
32]
Uint4B
+
0x2c0
SessionId :
Uint4B
+
0x2c8
AppCompatFlags :
_ULARGE_INTEGER
+
0x2d0
AppCompatFlagsUser :
_ULARGE_INTEGER
+
0x2d8
pShimData :
Ptr64
Void
+
0x2e0
AppCompatInfo :
Ptr64
Void
+
0x2e8
CSDVersion :
_UNICODE_STRING
+
0x2f8
ActivationContextData :
Ptr64
_ACTIVATION_CONTEXT_DATA
+
0x300
ProcessAssemblyStorageMap :
Ptr64
_ASSEMBLY_STORAGE_MAP
+
0x308
SystemDefaultActivationContextData :
Ptr64
_ACTIVATION_CONTEXT_DATA
+
0x310
SystemAssemblyStorageMap :
Ptr64
_ASSEMBLY_STORAGE_MAP
+
0x318
MinimumStackCommit :
Uint8B
+
0x320
FlsCallback :
Ptr64
_FLS_CALLBACK_INFO
+
0x328
FlsListHead :
_LIST_ENTRY
+
0x338
FlsBitmap :
Ptr64
Void
+
0x340
FlsBitmapBits : [
4]
Uint4B
+
0x350
FlsHighIndex :
Uint4B
+
0x358
WerRegistrationData :
Ptr64
Void
+
0x360
WerShipAssertPtr :
Ptr64
Void
+
0x368
pContextData :
Ptr64
Void
+
0x370
pImageHeaderHash :
Ptr64
Void
+
0x378
TracingFlags :
Uint4B
+
0x378
HeapTracingEnabled :
Pos
0,
1
Bit
+
0x378
CritSecTracingEnabled :
Pos
1,
1
Bit
+
0x378
SpareTracingBits :
Pos
2,
30
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
- 55.
- 56.
- 57.
- 58.
- 59.
- 60.
- 61.
- 62.
- 63.
- 64.
- 65.
- 66.
- 67.
- 68.
- 69.
- 70.
- 71.
- 72.
- 73.
- 74.
- 75.
- 76.
- 77.
- 78.
- 79.
- 80.
- 81.
- 82.
- 83.
- 84.
- 85.
- 86.
- 87.
- 88.
- 89.
- 90.
- 91.
- 92.
- 93.
So just change the offset directly ? Cough .... Surely not , as a result of vs stay x64 After compilation, it is no longer correct __asm{} Keywords recognized , If you want to continue using inline assembly , Some small configurations are needed : Refer to this article .
x64.asm Reference code :
We found that mov rax,gs:[60h] This line of code , Compare with the original mov eax, fs:[0x30] Offset by 0x30 Turned into 0x60, as a result of x64 Next _TEB Because of the different structure of :( As for the difference between registers, we won't discuss it here )
lkd
>
dt
!
_TEB
nt
!
_TEB
+
0x000
NtTib :
_NT_TIB
+
0x038
EnvironmentPointer :
Ptr64
Void
+
0x040
ClientId :
_CLIENT_ID
+
0x050
ActiveRpcHandle :
Ptr64
Void
+
0x058
ThreadLocalStoragePointer :
Ptr64
Void
+
0x060
ProcessEnvironmentBlock :
Ptr64
_PEB
// Look here !!!
+
0x068
LastErrorValue :
Uint4B
+
0x06c
CountOfOwnedCriticalSections :
Uint4B
+
0x070
CsrClientThread :
Ptr64
Void
+
0x078
Win32ThreadInfo :
Ptr64
Void
+
0x080
User32Reserved : [
26]
Uint4B
+
0x0e8
UserReserved : [
5]
Uint4B
+
0x100
WOW32Reserved :
Ptr64
Void
+
0x108
CurrentLocale :
Uint4B
+
0x10c
FpSoftwareStatusRegister :
Uint4B
+
0x110
SystemReserved1 : [
54]
Ptr64
Void
+
0x2c0
ExceptionCode :
Int4B
+
0x2c8
ActivationContextStackPointer :
Ptr64
_ACTIVATION_CONTEXT_STACK
+
0x2d0
SpareBytes : [
24]
UChar
+
0x2e8
TxFsContext :
Uint4B
+
0x2f0
GdiTebBatch :
_GDI_TEB_BATCH
+
0x7d8
RealClientId :
_CLIENT_ID
+
0x7e8
GdiCachedProcessHandle :
Ptr64
Void
+
0x7f0
GdiClientPID :
Uint4B
+
0x7f4
GdiClientTID :
Uint4B
+
0x7f8
GdiThreadLocalInfo :
Ptr64
Void
+
0x800
Win32ClientInfo : [
62]
Uint8B
+
0x9f0
glDispatchTable : [
233]
Ptr64
Void
+
0x1138
glReserved1 : [
29]
Uint8B
+
0x1220
glReserved2 :
Ptr64
Void
+
0x1228
glSectionInfo :
Ptr64
Void
+
0x1230
glSection :
Ptr64
Void
+
0x1238
glTable :
Ptr64
Void
+
0x1240
glCurrentRC :
Ptr64
Void
+
0x1248
glContext :
Ptr64
Void
+
0x1250
LastStatusValue :
Uint4B
+
0x1258
StaticUnicodeString :
_UNICODE_STRING
+
0x1268
StaticUnicodeBuffer : [
261]
Wchar
+
0x1478
DeallocationStack :
Ptr64
Void
+
0x1480
TlsSlots : [
64]
Ptr64
Void
+
0x1680
TlsLinks :
_LIST_ENTRY
+
0x1690
Vdm :
Ptr64
Void
+
0x1698
ReservedForNtRpc :
Ptr64
Void
+
0x16a0
DbgSsReserved : [
2]
Ptr64
Void
+
0x16b0
HardErrorMode :
Uint4B
+
0x16b8
Instrumentation : [
11]
Ptr64
Void
+
0x1710
ActivityId :
_GUID
+
0x1720
SubProcessTag :
Ptr64
Void
+
0x1728
EtwLocalData :
Ptr64
Void
+
0x1730
EtwTraceData :
Ptr64
Void
+
0x1738
WinSockData :
Ptr64
Void
+
0x1740
GdiBatchCount :
Uint4B
+
0x1744
CurrentIdealProcessor :
_PROCESSOR_NUMBER
+
0x1744
IdealProcessorValue :
Uint4B
+
0x1744
ReservedPad0 :
UChar
+
0x1745
ReservedPad1 :
UChar
+
0x1746
ReservedPad2 :
UChar
+
0x1747
IdealProcessor :
UChar
+
0x1748
GuaranteedStackBytes :
Uint4B
+
0x1750
ReservedForPerf :
Ptr64
Void
+
0x1758
ReservedForOle :
Ptr64
Void
+
0x1760
WaitingOnLoaderLock :
Uint4B
+
0x1768
SavedPriorityState :
Ptr64
Void
+
0x1770
SoftPatchPtr1 :
Uint8B
+
0x1778
ThreadPoolData :
Ptr64
Void
+
0x1780
TlsExpansionSlots :
Ptr64
Ptr64
Void
+
0x1788
DeallocationBStore :
Ptr64
Void
+
0x1790
BStoreLimit :
Ptr64
Void
+
0x1798
MuiGeneration :
Uint4B
+
0x179c
IsImpersonating :
Uint4B
+
0x17a0
NlsCache :
Ptr64
Void
+
0x17a8
pShimData :
Ptr64
Void
+
0x17b0
HeapVirtualAffinity :
Uint4B
+
0x17b8
CurrentTransactionHandle :
Ptr64
Void
+
0x17c0
ActiveFrame :
Ptr64
_TEB_ACTIVE_FRAME
+
0x17c8
FlsData :
Ptr64
Void
+
0x17d0
PreferredLanguages :
Ptr64
Void
+
0x17d8
UserPrefLanguages :
Ptr64
Void
+
0x17e0
MergedPrefLanguages :
Ptr64
Void
+
0x17e8
MuiImpersonation :
Uint4B
+
0x17ec
CrossTebFlags :
Uint2B
+
0x17ec
SpareCrossTebBits :
Pos
0,
16
Bits
+
0x17ee
SameTebFlags :
Uint2B
+
0x17ee
SafeThunkCall :
Pos
0,
1
Bit
+
0x17ee
InDebugPrint :
Pos
1,
1
Bit
+
0x17ee
HasFiberData :
Pos
2,
1
Bit
+
0x17ee
SkipThreadAttach :
Pos
3,
1
Bit
+
0x17ee
WerInShipAssertCode :
Pos
4,
1
Bit
+
0x17ee
RanProcessInit :
Pos
5,
1
Bit
+
0x17ee
ClonedThread :
Pos
6,
1
Bit
+
0x17ee
SuppressDebugMsg :
Pos
7,
1
Bit
+
0x17ee
DisableUserStackWalk :
Pos
8,
1
Bit
+
0x17ee
RtlExceptionAttached :
Pos
9,
1
Bit
+
0x17ee
InitialThread :
Pos
10,
1
Bit
+
0x17ee
SpareSameTebBits :
Pos
11,
5
Bits
+
0x17f0
TxnScopeEnterCallback :
Ptr64
Void
+
0x17f8
TxnScopeExitCallback :
Ptr64
Void
+
0x1800
TxnScopeContext :
Ptr64
Void
+
0x1808
LockCount :
Uint4B
+
0x180c
SpareUlong0 :
Uint4B
+
0x1810
ResourceRetValue :
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
- 55.
- 56.
- 57.
- 58.
- 59.
- 60.
- 61.
- 62.
- 63.
- 64.
- 65.
- 66.
- 67.
- 68.
- 69.
- 70.
- 71.
- 72.
- 73.
- 74.
- 75.
- 76.
- 77.
- 78.
- 79.
- 80.
- 81.
- 82.
- 83.
- 84.
- 85.
- 86.
- 87.
- 88.
- 89.
- 90.
- 91.
- 92.
- 93.
- 94.
- 95.
- 96.
- 97.
- 98.
- 99.
- 100.
- 101.
- 102.
- 103.
test.cpp Reference code :
#include "stdafx.h"
#include <iostream>
#include <windows.h>
#include <subauth.h>
#pragma
extern
"C"
PVOID64
_cdecl
GetPeb();
// quote .asm Functions in the file
#pragma
int
_tmain(
int
argc,
_TCHAR
*
argv[])
{
// obtain 64 position Peb Address
PVOID64
Peb
=
GetPeb();
std::
cout
<<
"Peb = "
<<
std::
hex
<<
Peb
<<
std::
endl;
// obtain BeingDebugged Address
BYTE
BeingDebugged
=
*(
BYTE
*)((
BYTE
*)
Peb
+
0x2);
std::
cout
<<
"BeingDebugged = "
<<
std::
hex
<< (
DWORD)
BeingDebugged
<<
std::
endl;
// obtain NtGlobalFlag Address
BYTE
NtGlobalFlag
=
*(
BYTE
*)((
BYTE
*)
Peb
+
0xbc);
std::
cout
<<
"NtGlobalFlag = "
<<
std::
hex
<< (
DWORD)
NtGlobalFlag
<<
std::
endl;
getchar();
return
0;
}
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
design sketch :

It's finished , Tomorrow Mid Autumn Festival , Remember to go home and have a look .(ノ゚∀゚)ノ
边栏推荐
- Open source SPL enhances mangodb computing
- leetcode-6130:设计数字容器系统
- Compilation and operation of program
- 程序的编译和运行
- 2022.7.24-----leetcode.1184
- Qixin Jushi cloud spectrum new chapter | Haitai Fangyuan and Sichuan Unicom reach ecological strategic cooperation
- [leetcode] 28. Implement strstr ()
- FanoutExchange交换机代码教程
- Leetcode customs clearance: hash table six, this is really a little simple
- Online XML to JSON tool
猜你喜欢

DDD的Go实战

preprocessor directives
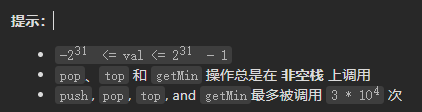
Leetcode-155: minimum stack

预处理指令

Remote - basic principle introduction
![[advanced drawing of single cell] 07. Display of KEGG enrichment results](/img/60/09c5f44d64b96c6e4d57e5f426e4ed.png)
[advanced drawing of single cell] 07. Display of KEGG enrichment results

Qixin Jushi cloud spectrum new chapter | Haitai Fangyuan and Sichuan Unicom reach ecological strategic cooperation

Leetcode-6127: number of high-quality pairs

基于腾讯地图实现精准定位,实现微信小程序考勤打卡功能
![[depth] the new LAAS agreement elephant: the key to revitalizing the development of the defi track](/img/ef/33f93225171e2c3e14b7d090c68196.png)
[depth] the new LAAS agreement elephant: the key to revitalizing the development of the defi track
随机推荐
Scan delete folder problems
Increase swap space
[technical dry goods] how to ensure the idempotency of the interface?
[cloud native] use of Nacos taskmanager task management
Pycharm跑程序时自动进入测试模式
从底层结构开始学习FPGA(16)----PLL/MMCM IP的定制与测试
How to use buffer queue to realize high concurrent order business (glory Collection Edition)
A detailed explanation of SCP command
Leetcode-114: expand binary tree into linked list
Explain the principle of MySQL master-slave replication in detail
The international summit osdi included Taobao system papers for the first time, and end cloud collaborative intelligence was recommended by the keynote speech of the conference
Unity VS—— VS中默认调试为启动而不是附加到Unity调试
一道golang中defer和函数结合的面试题
Recommend a website that converts curl commands into PHP code & a website that initiates and executes curl requests online
[workplace rules] it workplace rules | poor performance
Interpretation of filter execution sequence source code in sprigboot
Why did I choose to become a network engineer after graduating from weak current for 3 months
Introduction to MySQL engine and InnoDB logical storage structure
Illustration leetcode - 3. longest substring without repeated characters (difficulty: medium)
[MSA] a brief description of the moveit Configuration Assistant chain in planning groups