当前位置:网站首页>Istio II traffic hijacking process
Istio II traffic hijacking process
2022-07-24 20:00:00 【taoli-qiao】
Previously, I introduced Istio Rely on the Envoy How it works , Next, a practical example is given to demonstrate Istio How to complete traffic hijacking and traffic forwarding . First, prepare to deploy two pod, One nginx pod As a server , One toolbox pod As a client ,toolbox Just one can support linux Just a container for commands . Here are two pod Deployment file for . Start through the following file nginx and toolbox pod.
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
spec:
replicas: 1
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx
---
apiVersion: v1
kind: Service
metadata:
name: nginx
spec:
ports:
- name: http
port: 80
protocol: TCP
targetPort: 80
selector:
app: nginxapiVersion: apps/v1
kind: Deployment
metadata:
name: toolbox
spec:
replicas: 1
selector:
matchLabels:
app: toolbox
template:
metadata:
labels:
app: toolbox
access: "true"
spec:
containers:
- name: toolbox
image: centos
command:
- tail
- -f
- /dev/nullThen install on the cluster Istio. After successful installation, you can see 3 individual istio dependent pod Successful startup
curl -L https://istio.io/downloadIstio | sh -
cd istio-1.xx.0
cp bin/istioctl /usr/local/bin
istioctl install --set profile=demo -y
Then start the previously defined nginx and toolbox pod, If the namespace add to istio-injection=enabled The label of , Then the namespace Under the pod istio Will automatically inject .
kubectl create ns sidecar
kubectl label ns sidecar istio-injection=enabled
kubectl apply -f nginx.yaml -n sidecar
kubectl apply -f toolbox-default.yaml -n sidecarView started pod, You can see two pod Of container Quantity is no longer 1, It is 2.
Choose one by one pod for example toolboxpod, see pod Of details, You can see that except toolbox Self defined container Outside , It's started. istio-proxy Of container, This container The essence is to start a envoy Of proxy.

In addition to this container Outside , There's another. initcontainer, Yes Iptables Made some configuration changes .

Next, you can continue to see ,pod Medium iptables What does the configuration look like . On the left is the command view iptables The rules , On the right is to explain the meaning of each rule .
crictl pods|grep podName
//get containerId of pod
crictl inspectp containerId | grep pid
//get pid
nsenter -t pid -n iptables
//get iptables configuration By looking at iptables Rules can be known , For simulated clients toolboxpod Come on , If you want to access the service nginx, It means you want to send out a request , So according to iptables The rules , Will execute ISTIO_OUTPUT, and ISTIO_OUTPUT Suffocate again ISTIO_REDIRECT, ISTIO_REDIRECT Finally forward to 15001 On port .
By looking at iptables Rules can be known , For simulated clients toolboxpod Come on , If you want to access the service nginx, It means you want to send out a request , So according to iptables The rules , Will execute ISTIO_OUTPUT, and ISTIO_OUTPUT Suffocate again ISTIO_REDIRECT, ISTIO_REDIRECT Finally forward to 15001 On port .
Then check 15001 Port configuration information .
(istioctl pc listener -n sidecar toolbox-68f79dd5f8-q5nvd --port 15001 -ojson)
You can see 15001 It's a virtual port , Not a real service port , in addition , There are attributes in this configuration useOritinalDst=true Indicates forwarding to virtual port 15001 Request on , What is the original destination address , Then forward to 15001 After the , Still send the request to the original destination address , The original destination address is to visit nginx Service 80 port .

Then check 80 Port configuration information , see 80 port configuration , There is a real routing configuration , The routing configuration name is routeConfigName=80.
(istioctl pc listener -n sidecar toolbox-68f79dd5f8-q5nvd --port 80 -ojson)

Then check that the route name is equal to 80 Configuration information , There are many routing configuration information in this configuration file , It's about nginx Of , If it's a visit nginx, Well, let's go cluster=nginx.sidecar.svc.cluster.local Handle ( One thing to note , Described above envoy I mentioned envoy in cluster The meaning of is a pile ip A collection of addresses )
(istioctl pc route -n sidecar toolbox-68f79dd5f8-q5nvd --name=80 -ojson)

Then check cluster Contains IP The address information will know the destination of the final request IP Address .
istioctl pc cluster -n sidecar toolbox-68f79dd5f8-8gkp9
istioctl pc endpoint -n sidecar toolbox-68f79dd5f8-8gkp9

Cluster The target address included is nginx service Pod The address of . So the final request can be sent to nginx On . When the request is sent out , Eventually follow iptables The rules of , Look again iptables The rules of , There is a outbound The rule is : If owner=1337, Then send it out directly , and envoy The process number of is 1337

The above describes in detail the process of sending the request , For the server, it is to receive requests , namely Iptables What's going on is Inbound The rules of . about Inbound Request , adopt iptable The request will be sent to envoy Of 15006 On port , The service that this port finds needs to be accessed is the service that exists on this machine , So forward the request to the local nginx pod Handle .

For the top toolbox( Simulation client ),nginx( Simulation server ) The schematic diagram of the access relationship of is as follows :
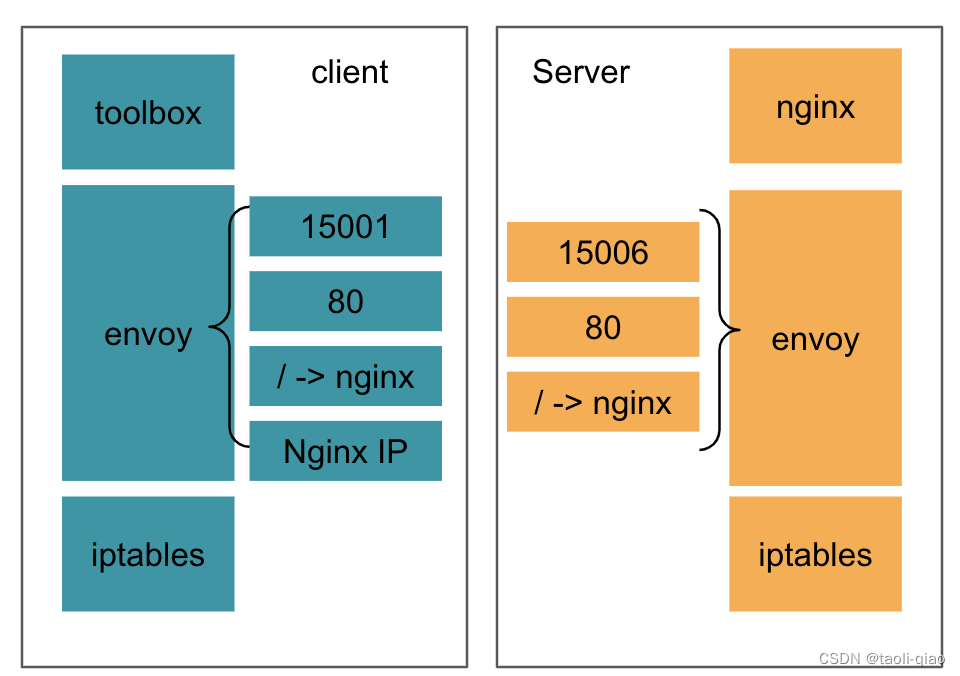
about Istio sidecar Schematic diagram of traffic hijacking , Here is a detailed diagram , The example used is Istio Official website bookInfo application .

That's right Istio sidecar How to explain traffic hijacking , Thoroughly understand the process of traffic hijacking , It is helpful in real projects if the traffic does not enter the expected destination address , Then group level troubleshooting can be carried out .
边栏推荐
- Maya coffee machine modeling
- 拿捏C指针
- Leetcode 146: LRU cache
- Microservice architecture | service monitoring and isolation - [sentinel] TBC
- [face to face experience of school recruitment] 8 real questions of pointer interview. Come and test how many you have mastered.
- Review the code implementation of memcpy function
- Functional test of redisgraph multi active design scheme
- 从服务器批量下载文件到本地
- Istio二之流量劫持过程
- Duilib actual combat 1- imitate Baidu online disk login interface
猜你喜欢

Create a life cycle aware MVP architecture

Virtual machine win7 system installation vmtool

Leetcode652 finding duplicate subtrees

Interface component devaxpress asp Net v22.1 - new office 365 dark theme

Batch download files from the server to the local

Description of large and small end mode

LSTM and Gru of RNN_ Attention mechanism

原反补及大小端

Basic idea of regularization

Pix2seq: Google brain proposes a unified interface for CV tasks!
随机推荐
Batch download files from the server to the local
Redis common configuration description
Detailed explanation of ELF format (I)
Look at the interface control devaxpress WinForms - how to customize auxiliary function properties (Part 2)
Conversion between VC string and timestamp
How to export map files tutorial
Day 5 (array)
Sword finger offer 45. arrange the array into the smallest number
Unity3d eventsystem (event)
872. Maximum common divisor
Siyuan notes V2.1.2 synchronization problem
Unity2d~ game practice of decrypting Zhou mu (completed in three days)
Valdo2021 - vascular space segmentation in vascular disease detection challenge (I)
Introduction to fastdfs high availability
Original reverse compensation and size end
2019 Hangzhou Electric Multi School Game 9 6684 Rikka with game [game question]
Decision tree_ ID3_ C4.5_ CART
Hidden Markov model HMM
Ask a question: is there an error msg = ora-04036: instance usage when using CDC to monitor oracle
Mysql8.0 learning record 19 - Page segments and tablespaces